5 minutes
FITE7410 Introduction to Financial Fraud Analytics
Introduction to Financial Fraud
Basic introdution (according to reports)
- types of crime (according to PwC)
- accounting/financial statement fraud
- anti-competition/antitrust law infringement
- bribery and corruption
- customer fraud
- cybercrime
- deceptive business practices
- human resources fraud
- insider/unauthorized trading
- intellectual property (IP) theft
- money laundering and sanctions
- procurement fraud
- interesting phenomenon
- approxiamtely 50% of companies experienced fraud in the past 2 years
- but only 56% of companies conducted investigations into their worst incidents
Fraud
- definition
- no formal definition
- English dictionary definition
- the crime of getting money by deceiving people
- legal dictionary definition
- the intentional use of deceit, a trick or some dishonest means to deprive another of his/her/its money, property or a legal right
- types of financial frauds
- no single definition
- categorization (by FBI)
- bank fraud
- credit card fraud
- application fraud
- obtain new credit cards using false personal information
- spending as much as poosible in a short time
- behavioral fraud
- stole details of credit cards (not physical card), using on a “cardholder not present” basis
- most common type
- application fraud
- mortgage fraud
- money laundering
- make illegally obtained gain and proceeds seemingly legal
- AML (Anti-Money Laundering) compliance is mandatory requirements for running business in the financial sector
- credit card fraud
- corporate fraud
- financial statement fraud
- represent fake financial condition of a company
- deveive or mislead to the users of the financial statements
- e.g. Enron
- securities and commodities fraud
- financial statement fraud
- insurance fraud
- any types of insurance
- automobile insurance fraud (by FBI)
- health care fraud (by FBI)
- from the issuer (seller)
- selling policies from non-existent companies
- failing to submit premiums
- churning policies to create more commissions
- from the buyer
- exaggerated claims
- falsified medical history
- post-dated policies
- faked death
- faked damage
- any types of insurance
- bank fraud
- other types
- identity theft
- replace someone to make transactions or purchases
- stealing lists of customer information
- tax evasion
- underpay taxes
- securities fraud
- a false statement about a company or company’s valued stock
- others make decisions based on that lie
- identity theft
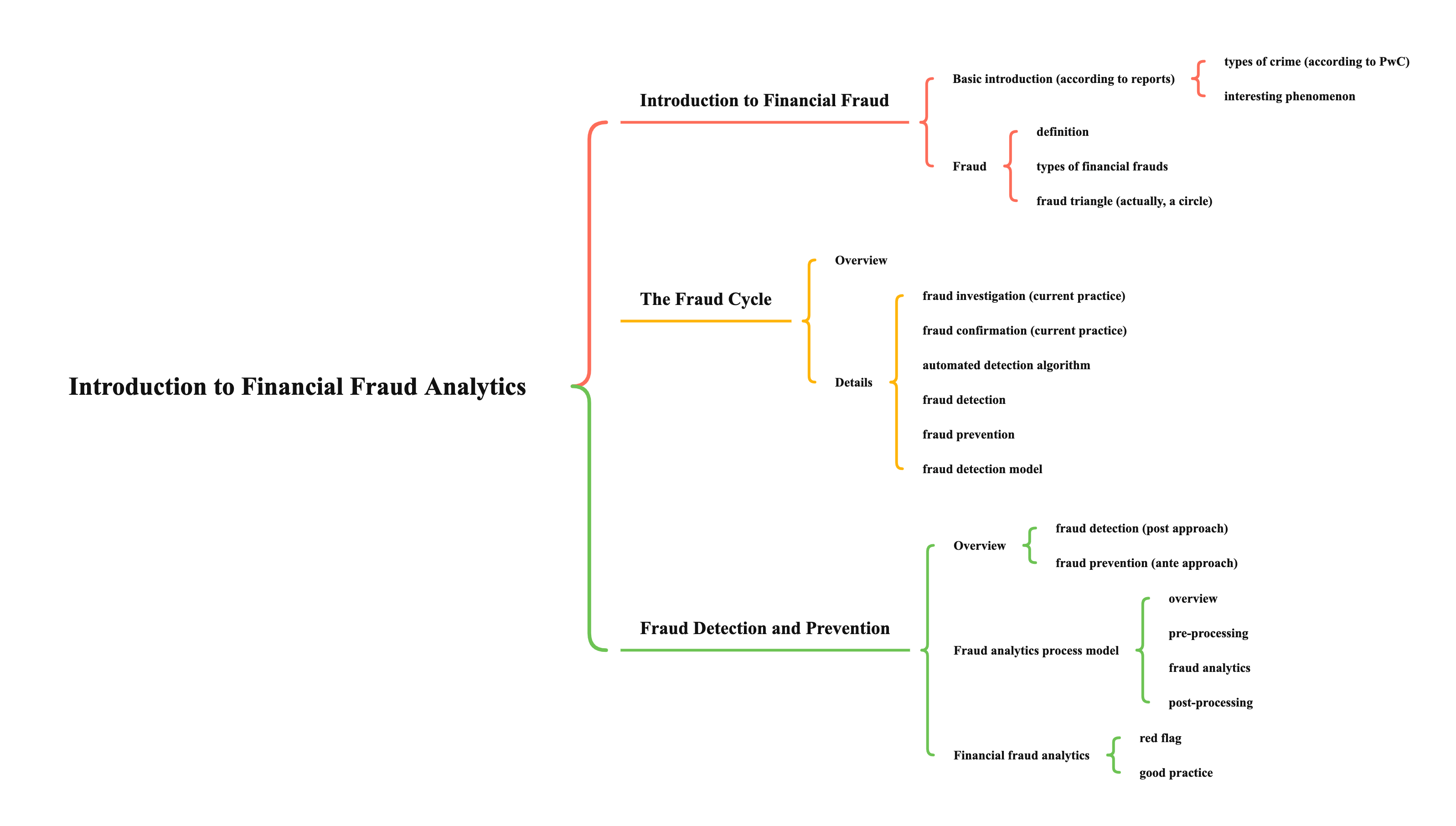
- fraud triangle (actually, a circle)
- pressure
- from financial, social, or any other nature
- it cannot be resolved or relieved in an authorized manner
- opportunity
- opportunity exists to resolve or relieve the experienced pressure in an unauthorized but concealed or hidden manner
- rationalization
- pyschological mechanism, explain why fraudsters do not refrain
- think conduct as acceptable
- pressure
The Fraud Cycle
Overview
Details
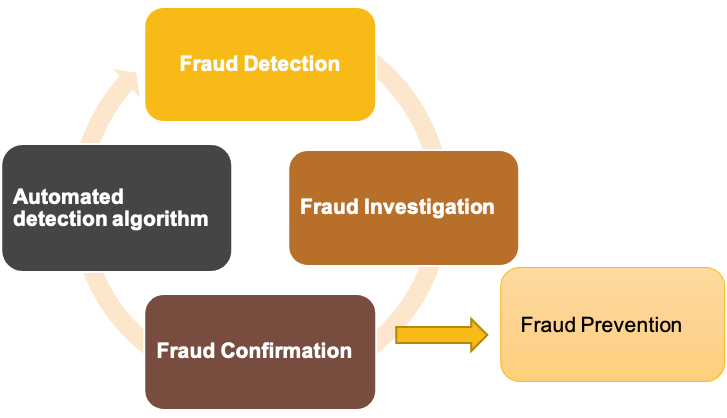
- fraud investigation (current practice)
- a human expert investigates suspicious, flagged cases
- fraud confirmation (current practice)
- determine true fraud label
- after this, 2 measures will be taken
- corrective measures
- resolve the fraud and correct the wrongful consequences -> fix
- preventive measures
- preventing future fraud by the same fraudster or others -> prevent
- corrective measures
- automated detection algorithm
- newly detected cases should be addded to the database of historical fraud cases -> optimize the model
- fraud detection
- apply detection model on new, unseen observations
- assign a fraud risk to every observation
- fraud prevention
- prevent fraud in the future
- detect or predict fraud before it happens
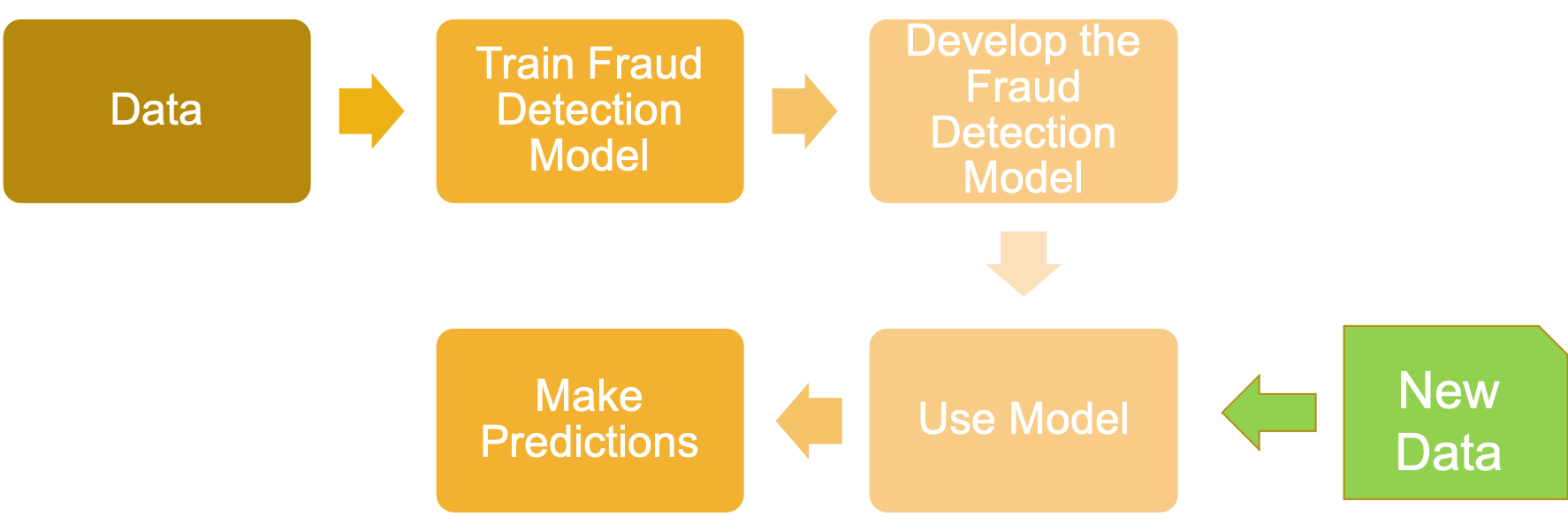
- fraud detection model
- frequency of re-training the model depends on
- volatility of the fraud behaviour
- detection power of the current model
- amount of (similar) confirmed cases already available in the database
- rate at which new cases are being confirmed
- required effort to retrain the model
- frequency of re-training the model depends on
Fraud Detection and Prevention
Overview
- fraud detection (post approach)
- recognize or discover fradulent activities
- traditionally, expert-based approach
- depends on a human’s professional knowledge to build a number of rule-based engines (IF…, THEN…)
- disadvantages
- expensive to build -> manual input
- difficult to maintain -> manually and regularly updated
- slow response time to new fraud cases -> expert needs to study new fraud cases
- prone to human error -> relies heavily on human expert
- reasons for using data driven fraud detection
- precision
- process massive volumes of data
- more efficient than human eyes
- operational efficiency
- process a huge amount of cases in a short time
- cost efficiency
- compared with expert-based system, better cost efficiency and ROI
- precision
- fraud prevention (ante approach)
- avoid or reduce fraud
- complementary to fraud detection, not independent of fraud detection
Fraud analytics process model
- overview
- is not a linear process but a cyclic process
- one may go over to the previous steps during the process
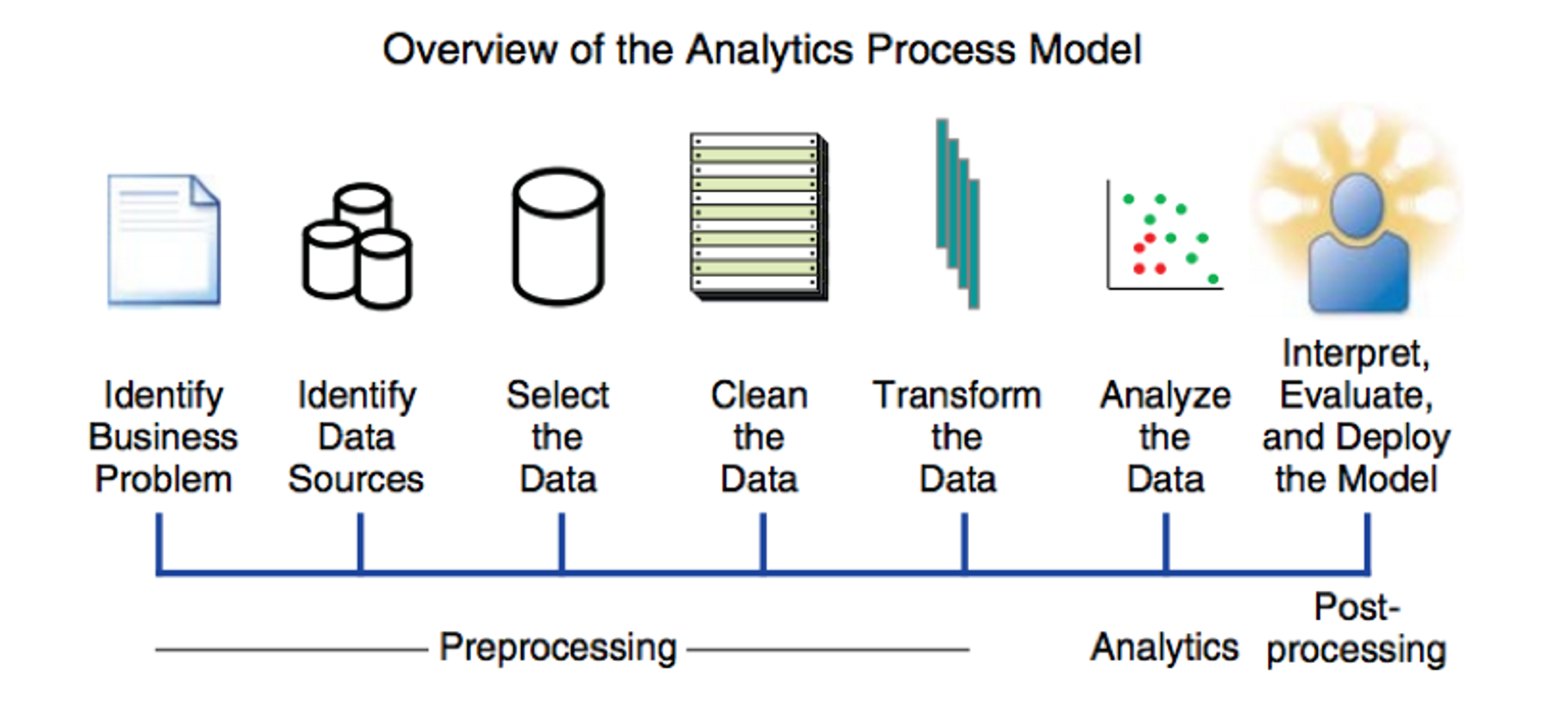
- pre-processing
- identify business problem is the most important task in this part
- fraud analytics
- techniques used
- expert-based techniques
- statistical techniques
- AI/data mining/machine learning techniques
- techniques used
- post-processing
- key characteristics of a good fraud analytics model
- statistical accuracy
- accuracy is not the only parameter, e.g. capacity or capability of the model
- statistically significant, i.e. the patterns found is not the consequence of coincidence
- interpretability
- black-box models are acceptable
- operational efficiency
- real-time evaluation
- re-estimate the model when necessary
- economical cost
- tech and human cost of building models
- regulatory compliancy
- should comply with all regulation and legislation, e.g. privacy laws
- statistical accuracy
- key characteristics of a good fraud analytics model
Financial fraud analytics
- red flag
- anomality or variation from predictable patterns of normal behavious
- exist in
- data
- documents
- internal controls
- behaviors
- public records
- digital footprints, etc.
- examples
- tax evasion fraud
- an identical financial statement, copy nonfraudulent companies
- name of an accountant is unique, this accountant may not exist
- credit card fraud
- a small payment followed by a large payment immediately after, test the card is still active
- regular rather small payments, may avoid getting noticed
- tax evasion fraud
- good practice
- plan before acting
- well-defined scope for fraud analytics
- good understanding of fraud data
- distinguish red flags and error in data
- identify false positives and fasle negatives
- e.g. someone uses credit card to purchase frequently in Dec, which may be not fraud due to Christmas
- try not to jump to conclusions without correct and logical linkage to evidence found