10 minutes
ICOM6045 Access Control
Introduction
- access control: deals with the prevention and detection of unauthorized actions by users of a computer system
indentification and authentication: stating who you are and proving the identification claim with credentials
- username (identification) and password (authentication)
other authentication techniques
- something you know, e.g. password
group password criteria try to crack the passwords A passwords consists of >= 6 characters, with at least 1 non-letter 30% easy to crack (passwords easy to remember) B passwords based on passphrases 10% were cracked (passwords easy to remember) C passwords consists of 8 randomly selected characters 10% were cracked (passwords difficult to remember) - something you have, e.g. smartcard
- using pin and card to verify identity
- something you are, e.g. biometric
- enrollment/registration: recording of fingerprint info
- fingerprint is captured by a device
- features are extracted and recorded in a database
- verification/identification: checking of a fingerprint
- features are compared with those in database
- known-subject matching: match with one stored fingerprint features record
- unknown-subject matching: match all records to find records with similar features (more on investigation, less popular)
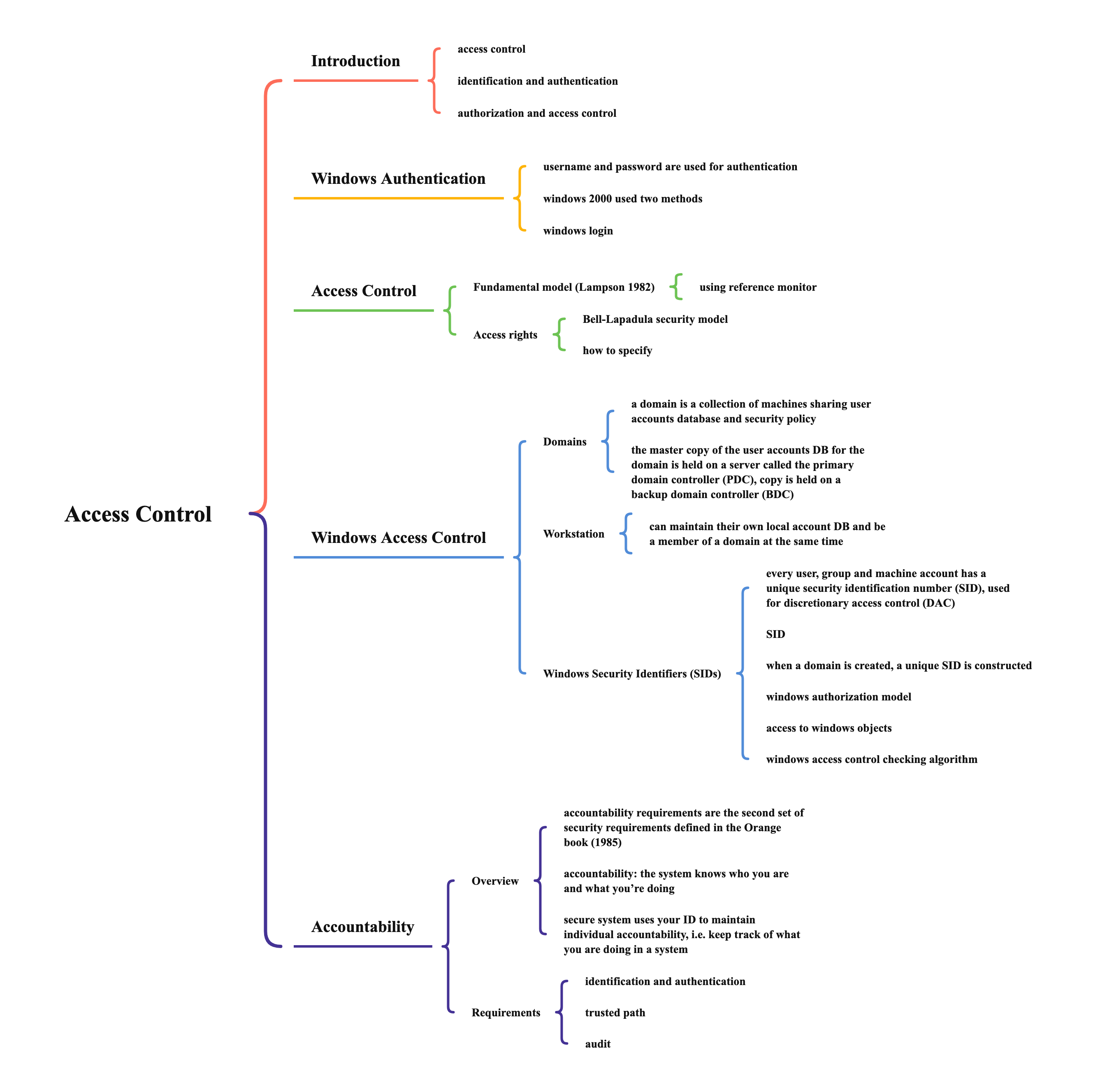
- types of features
- global features: patterns (aggregate characteristics of ridges)
- arch: ridges enter from one side of the finger, rise in the center forming an arc, and then exit the other side
- loop: ridges enter from one side of a finger, form a curve, and tend to exit from the same side they enter
- whorl: ridges form circularly around a central point on the finger
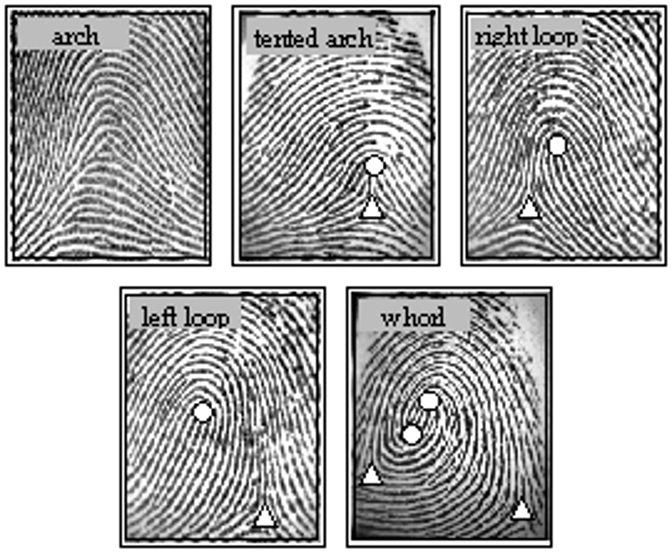
- local features: minutiae (difficult)
- ridge ending
- bifurcation
- short ridge (or dot)
- global features: patterns (aggregate characteristics of ridges)
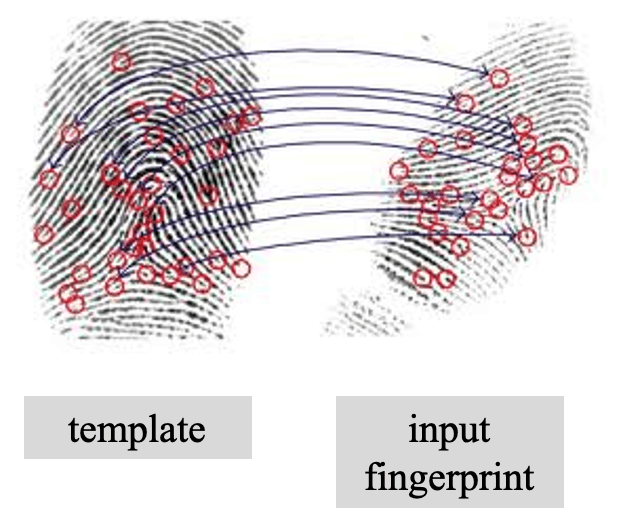
- fingerprint minutiae matching
- minutiae are extracted from the 2 fingerprints and stored as sets of points in the 2-dimensional plane
- each minutia is stored as a triplet {x, y, θ}, where (x, y) is the minutia is the location coordinate and θ is the minutia angle
- formulated as a “point pattern matching” problem and processed by pattern recognition algorithm
- fingerprint scanner would check, e.g. iPhone
- fingerprint, verify whether it is correct
- alive, the finger is alive, not just cut one from others (so artificial finger cannnot unlock)
- features are compared with those in database
- enrollment/registration: recording of fingerprint info
- something you know, e.g. password
definitions
- subject: a user
- credential: the required proof needed by the system to validate the identity of the user, e.g. the password
- principal: a name associated with a subject, e.g. username
- subject can have multiple names, e.g. different username on different machine
authorization and access control: restriction on the ability of a subject to use a system or an object in that system
Windows Authentication
- username and password are used for authentication
- windows 2000 uses two methods
- MSV1_0
- stand-alone station
- simple
- just username and hashed password
- do matching with SAM (security account manager)
- match -> success
- no match -> fail
- SAM: the encrypted passwords are stored in the user accounts which are held in the SAM database
- the SAM database is part of the registry
- a binary life, accessed using SAM APIs
- each password is hashed using a one-way function, i.e. password cannot be retrieved in plain form (if you forget your password, you lose it)
- CTRL+ALT+DEL
- aka “secure attention key”: generates calls to low-level functions that cannot be duplicated by application programs
- invokes the Windows operating system logon screen
- provides a trusted path from the keyboard to the login process (winlogon.exe)
- Kerberos
- network environment users
- KDC (key distribution center)
- authenticates users at login and issues tickets which are valid for one session
- maintain a database of secrect keys of all users
- two components
- AS (authentication server): aka. Kerberos server, verify who you are
- a user presents an authenticating credential (e.g. password) to the authentication server
- AS returns a ticket to the user showing that the user has passed authentication
- TGS (ticket granting server): give you personal ticket, using this to access the resource (different people have different tickets, due to AS)
- a users wants to access a resource R (e.g. a file), he sends his authenticated ticket and a request to use R to TGS
- the TGS returns 2 tickets to the user: one shows that the user’s access to R is authorized, the other is for the user to present to R in order to access R
- AS (authentication server): aka. Kerberos server, verify who you are
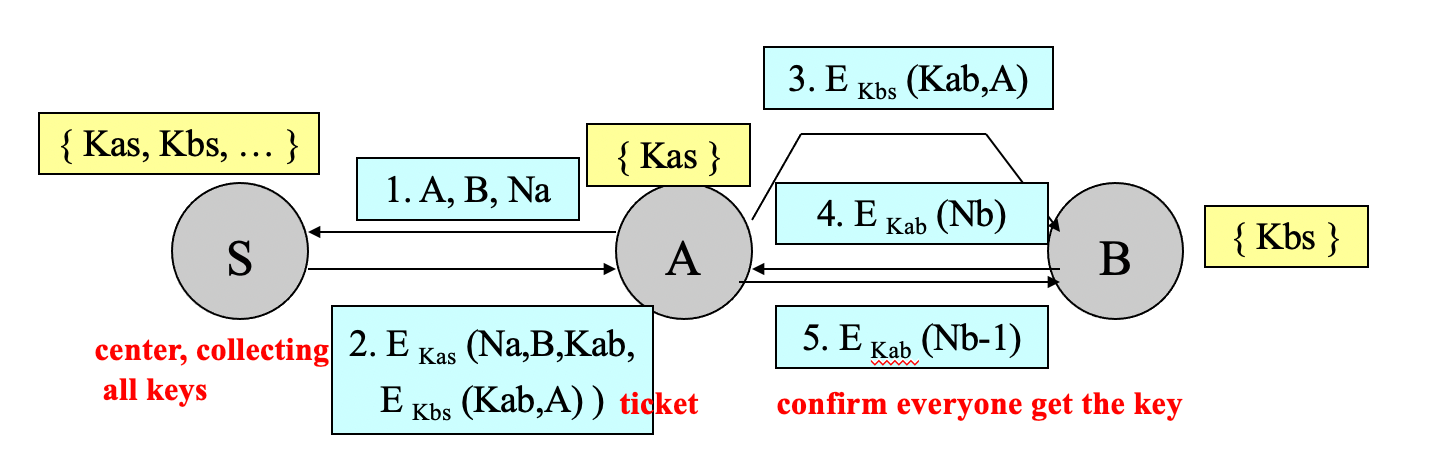
- Needham and Schroeder Protocol
- a key exchange protocol used in Kerberos
- based on symmetric key crytography
- setting
- Kab: session key between A and B
- Na, Nb: random numbers, avoid sending request again and again
- \(E_K(M)\): encrypt M using K
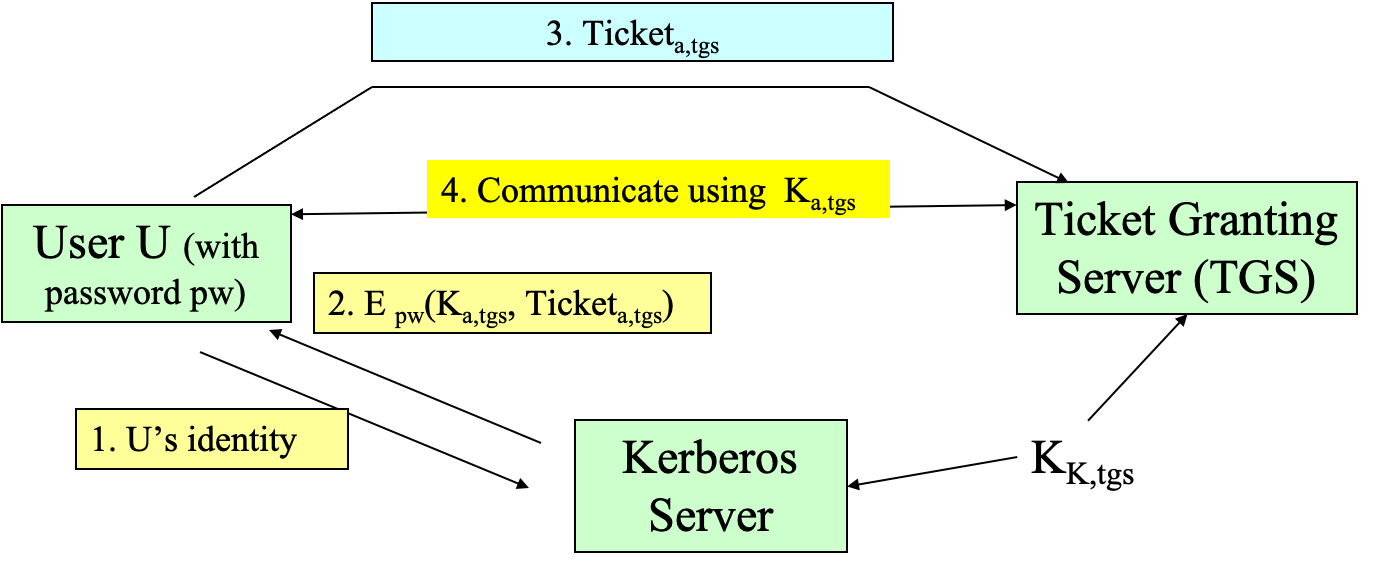
- Kerberos Authentication Protocol initiating a Kerberos session
- user U with password pw
- Kerberos server: store (U, pw)
- \(K_{K,tgs}\): the secret key shared between Kerbers server and TGS
- \(K_{a,tgs}\): the session key to be used between U and TGS
- \({Ticket}_{a,tgs}\): contains the session key \(K_{a,tgs}\) encrypted using \(K_{K,tgs}\)
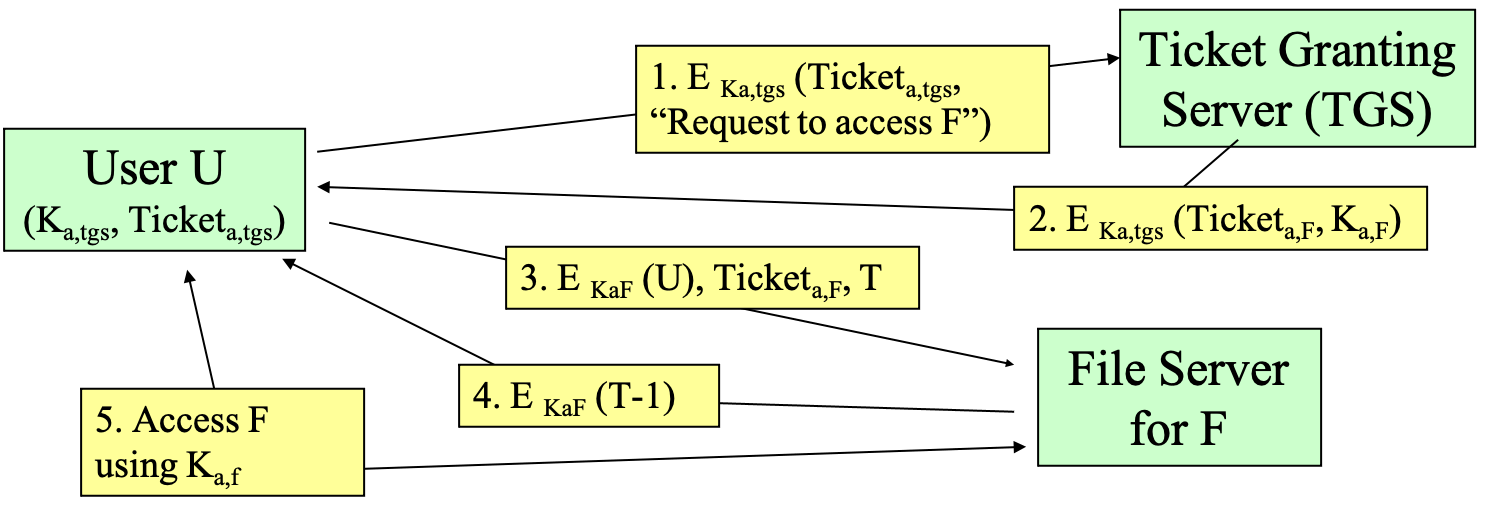
- Kerberos Authentication Protocol access a file (after communicating with TGS)
- \(Ticket_{a,F}\) encrypted by \(K_{F,tgs}\), contains
- U's authenticated identity
- an identification of F
- access rights of F with respect to U
- the session key \(K_{a,F}\) for communication between file server and U
- an expiration date for the ticket
- do not need any public key cryptography, just ticket
- \(Ticket_{a,F}\) encrypted by \(K_{F,tgs}\), contains
- advantages
- no password communicated on the network
- protected against spoofing using symmetric key encryption
- limited period of validity for each ticket: protect against brute force search
- timestamps to prevent replay attack
- mutual authentication
- some issues
- requires continuous availability of a trusted TGS (centralized)
- requires a trusted relationship between TGS and every server
- requires timely transactions
- password guessing works
- MSV1_0
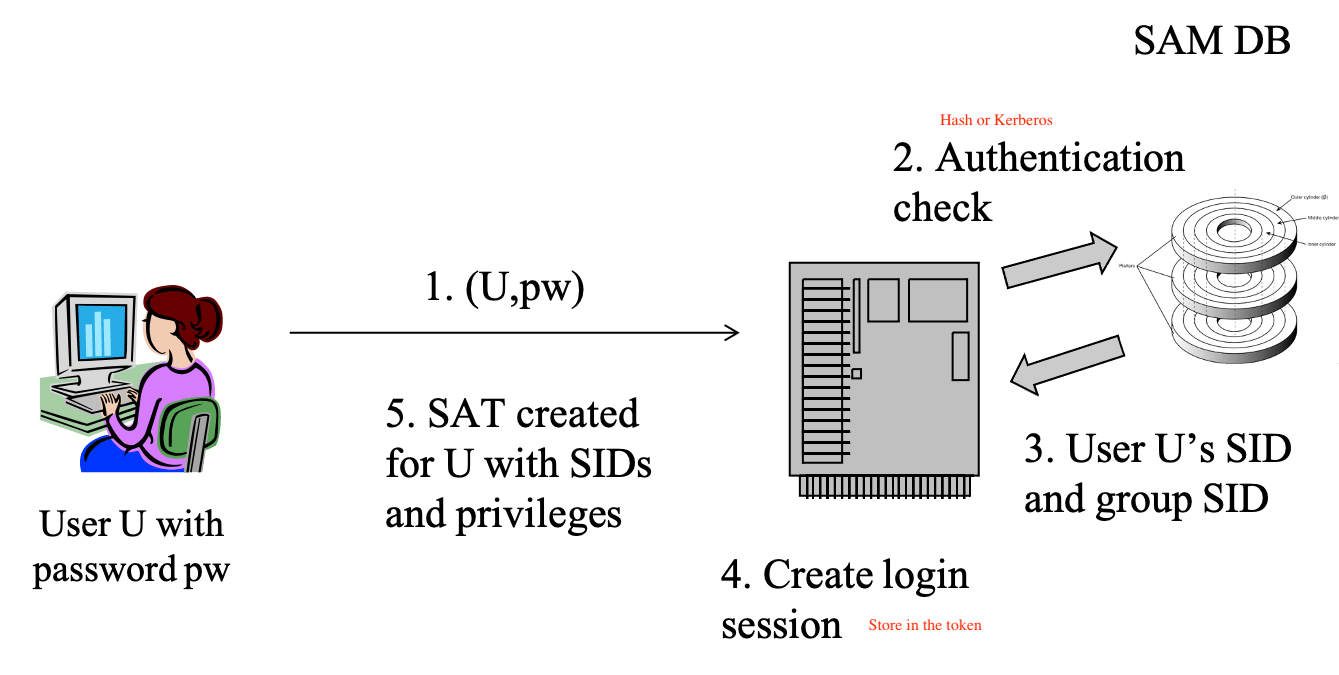
- windows login
- users are prompted for username and password
- username and password are gathered by the login process and passed on to the Local Security Authority (LSA) module
- the LSA calls the authentication package that compares the username and password against the values stored in SAM
- when a match is found, the SAM returns the user’s security ID (SID) and the security ID of any group the user belongs to
- the authentication package creates a login session and passes this session together with all SIDs back to the LSA
- the LSA creates a system access token (SAT), containing the user’s SIDs and user rights (privileges)
- the access token contains all relevant information about the capabilities of the authenticated user
- when deciding whether the user is allowed for a particular access, the access token will be consulted
Access Control
Fundamental model (Lampson 1982)
- using reference monitor
- how to specify the control
- what a subject is allowed to do: used in typical application system
- e.g., user A is allowed to access database table T
- what may be done with an object: used by typical OS
- e.g., file gcc is executable and accessible by everyone
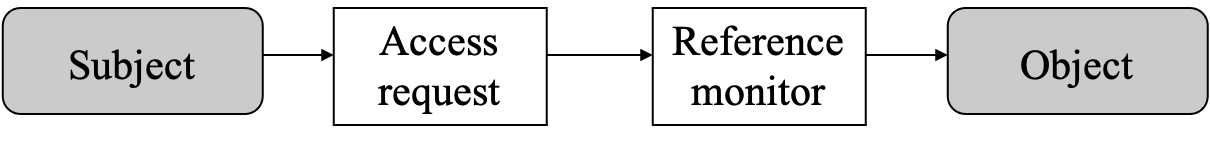
- e.g., file gcc is executable and accessible by everyone
- what a subject is allowed to do: used in typical application system
- how to specify the control
Access rights
- Bell-Lapadula security model
- 4 access rights
- execute
- read
- append (blind write), e.g., transaction log
- write
- cannot access
- 4 access rights
- how to specify
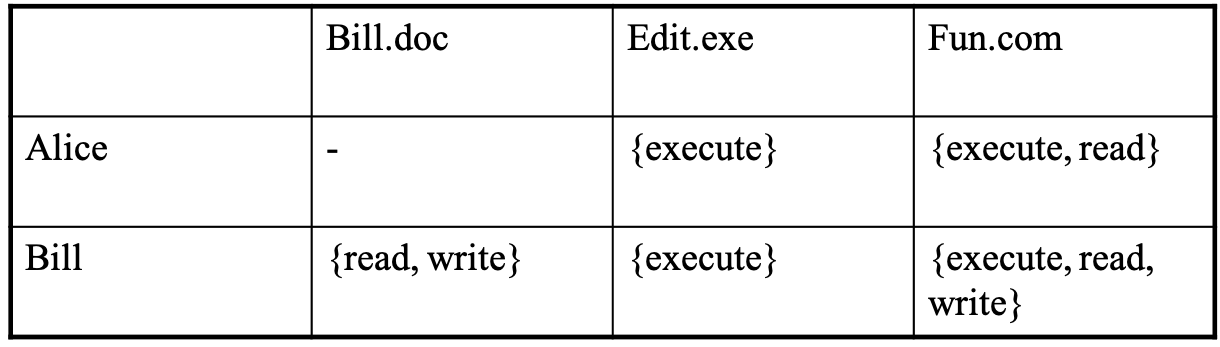
- access control matrix (not use)
- can write zero bits in a file to achieve delete function, so there is no rights called "delete" or "move"
- too tedious
- capabilities (not use)
- disadvantages
- difficult to get an overview of who has permission to access a given object, e.g. who has read access to Fun.com
- difficult to revoke a capability: either the OS has to be given the task or users have to keep track of all the capabilities they passed on

- disadvantages
- access control lists (windows use this)
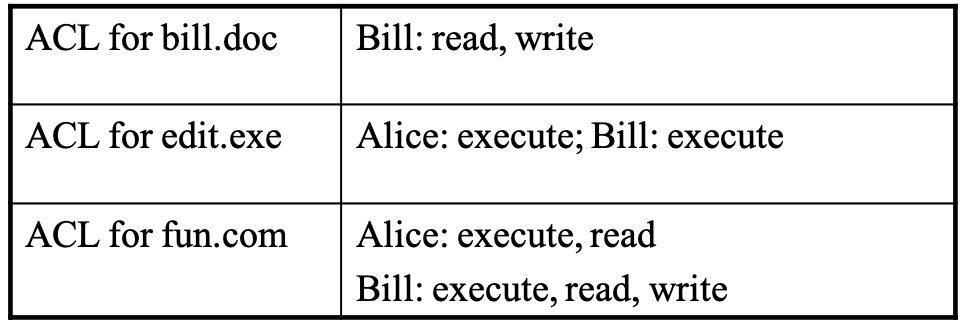
- group
- today, we often use the ACL and group together
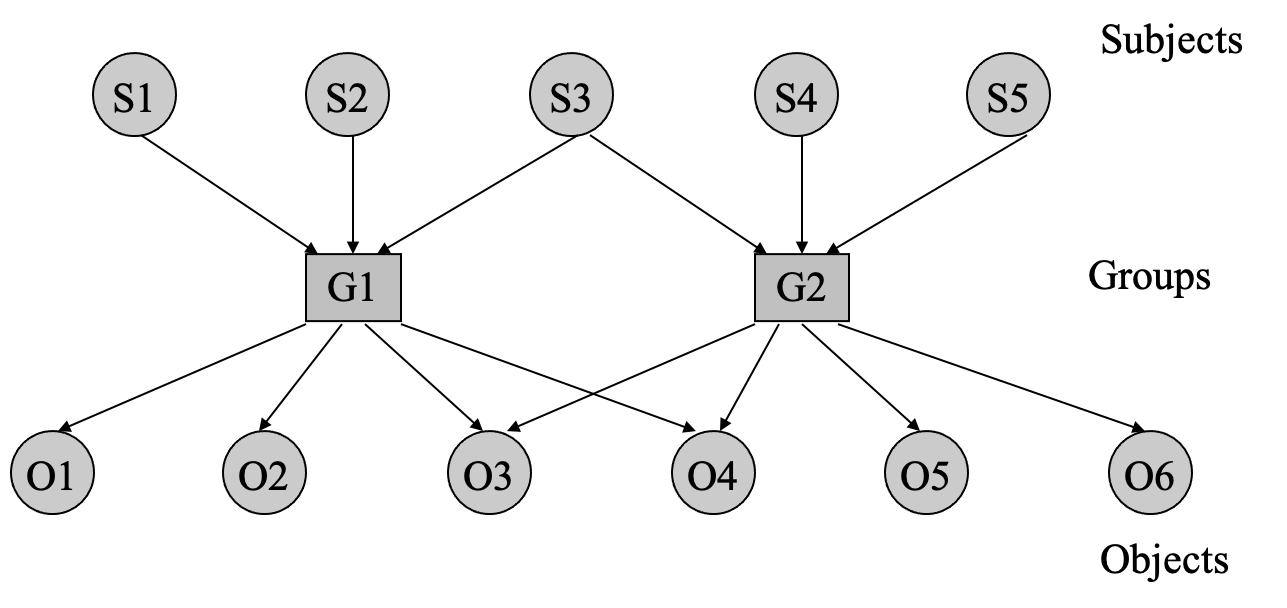
- today, we often use the ACL and group together
- role-based access control
- very common in application layer
- subjects derive their access rights from the role they are performing
- objects: each object can be accessed only through the procedures defined for the object
- roles
- a role is a collection of application specific operations (procedures)
- roles are assigned to users
- a user can have more than one role and more than one user can have the same role
- some problems
- possible violation of security policy due to role inheritance, automatic assumption of rules, unrestricted grants of privileges
- possible misconfiguration due to fuzzy nature of overlaps between roles:
- assignment of users to multiple roles
- assignment of objects to multiple object-access groups
- access control matrix (not use)
Windows Access Control
Domains
- a domain is a collection of machines sharing user accounts database and security policy
- the master copy of the user accounts DB for the domain is held on a server called the primary domain controller (PDC), copy is held on a backup domain controller (BDC)
Workstation
- can maintain their own local account DB and be a member of a domain at the same time
- user can be a local user or a global user
- a user with a local and a global account will have 2 different security identifiers (2 SIDs)
- resources can be managed globally or locally, e.g., a local printer or a network printer
Windows Security Identifiers (SIDs)
- every user, group and machine account has a unique security identification number (SID), used for discretionary access control (DAC)
- DAC means you create a document, and you can control it
- but if you are a general in military, the result may be opposite
- DAC means you create a document, and you can control it
- SID
- constructed when the account is created
- fixed for the life time of the account
- pseudo-random inputs are used in its construction, i.e. delete an account and recreate it will not have the same SID, and access permissions will be different
- structure (S-R-I-S-S- … -RID)
- R: revision number (currently 1)
- I: identifier authority (48-bit)
- S: 1-14 subauthority fields (32-bit)
- RID: relative 32-bit identifier, unique in authority’s name space
- typical principals with their SID
- everyone (world): S-1-1-0
- system: S-1-5-18: the Windows on a machine runs locally as S-1-5-18
- administrator: S-1-5-21-<local authority>-500: a user account created during Windows installation
- administrators: S-1-5-32-544: built-in group with administrator privileges
- guest: S-15-21-<authority>-501
- when a domain is created, a unique SID is constructed
- when a workstation or a server joins a domain, it receives a SID that includes the domain’s SID
- copying the root directory and configuration files of one machine to another machine will make the 2 machines have identical SIDs, which violates the Windows security policy
- windows authorization model
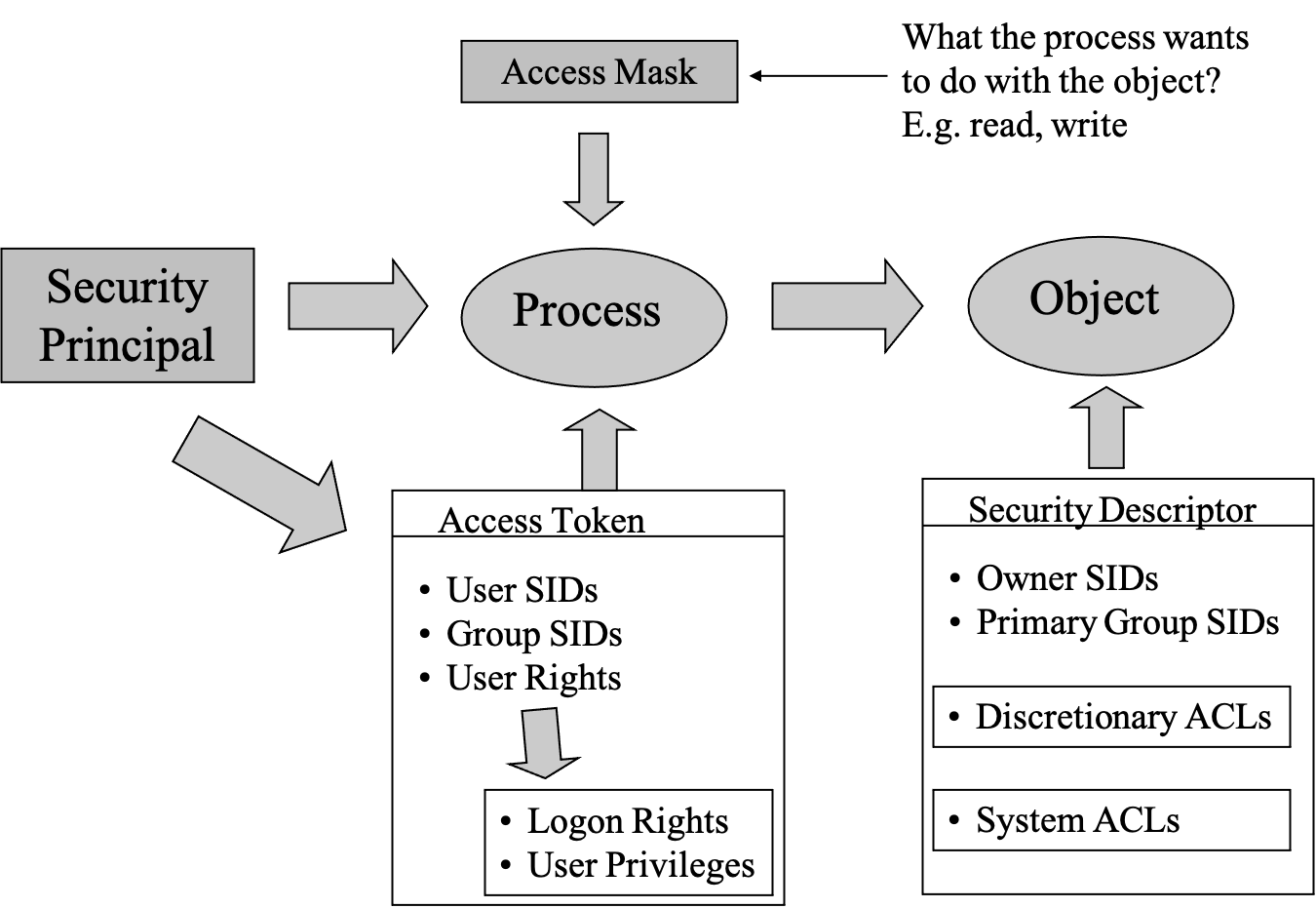
- access to windows objects
- each object has a security descriptor
- the security ID of the owner of the object and the primary group SID
- a set of discretionary access control lists (ACLs): contains access control permissions
- a set of system access control list: contains auditing permissions, which control the audit messages to be generated
- an ACL is composed of multiple Access Control Entries (ACEs), each ACE is a permission
- an access control list entry (ACE) for a subject or group can be
- AccessDenied: always listed first in an ACL
- AccessAllowed: a list of access permission
- each object has a security descriptor
- windows access control checking algorithm
- if no ACL exists, no checks are performed and access is granted
- if an ACL exists, then for each ACE, the subject’s SID in the SAT is compared with the SIDs in the ACE:
- the ACE does not contain a matching SID, the ACE is skipped
- the ACE contains a matching ID specifying ‘AccessDenied’, no access is permitted, regardless of any conflicting AccessAllowed flags
- the ACE contains a matching SID specifying ‘AccessAllowed’, access is granted
- if no matching entry is found, access is denied
Accountability
Overview
- accountability requirements are the second set of security requirements defined in the Orange book (1985)
- accountability: the system knows who you are and what you’re doing
- the system must be able to identify all users of the system
- the system must use information about your identity to decide whether you can access certain information
- the system must keep track of any security-related actions you take
- secure system uses your ID to maintain individual accountability, i.e. keep track of what you are doing in a system
- e.g., if KPC repeatedly tries to access files he’s not authorized to view, the system will know
Requirements
- identification and authentication
- proof yourself to TCB (trusted computing base, mechanisms that enforce security in a system)
- trusted path
- proof you connect to the correct institutions, i.e. authenticate the secure system
- in the past, we use particular key sequence
- today, we use public key certificate
- audit
- the recording, examining and reviewing of security related activities in a trusted system
- typical events are
- logons (successful or unsuccessful)
- logouts
- remote system accesses
- file opens, closes, renames, and deletions
- changes in privileges or security attributes
- auditing provides a way of determining whether and how an attack may take place