4 minutes
ICOM6045 Application Layer Security
Host-Based Intrusion Detection
Motivations and basis
- motivations
- collection of information about intrusion techniques that can be used to strengthen the intrusion prevention facility
- basis
- the behavior of intruders differs from that of a legitimate user in a quantifiable way
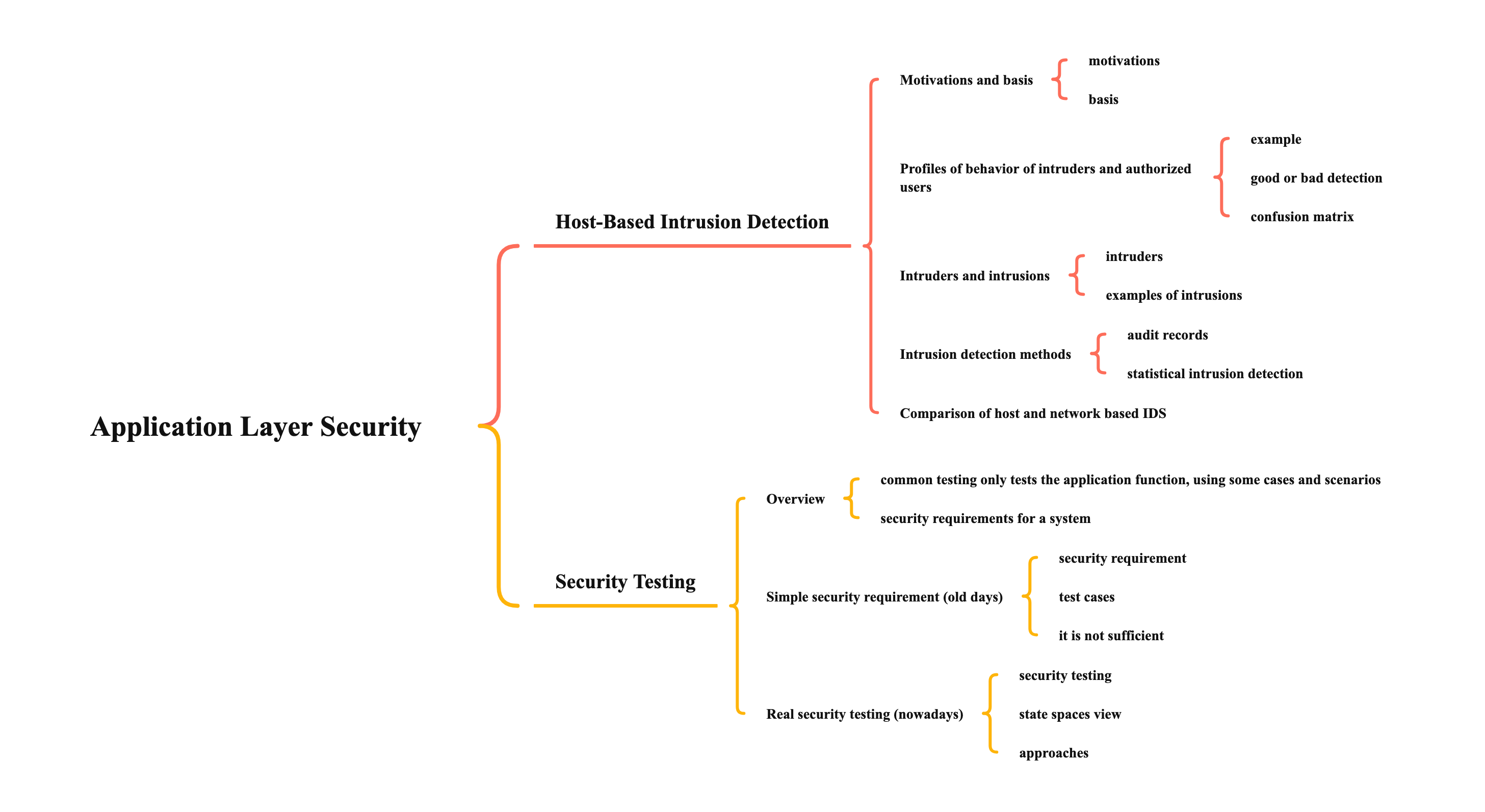
Profiles of behavior of intruders and authorized users
- example
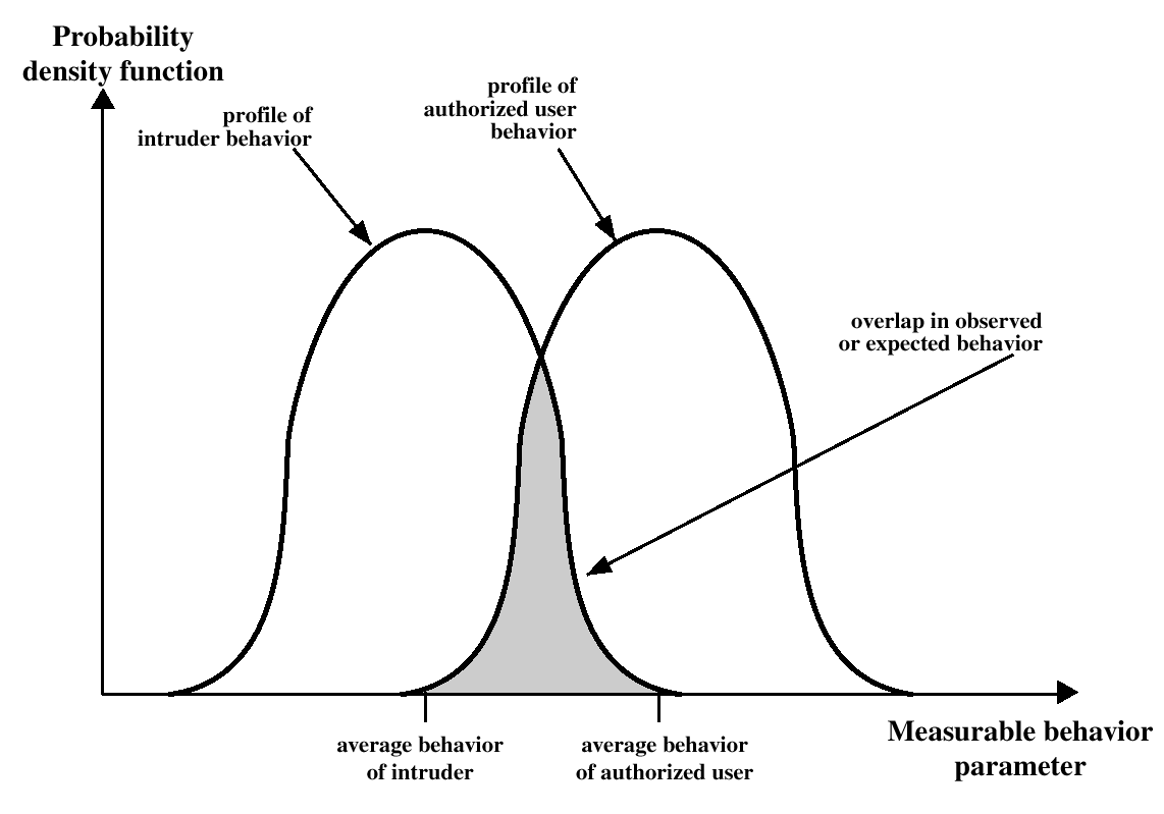
- good or bad detection
- confusion matrix
- intrusion detection


- intrusion detection
Intruders and intrusions
- intruders
- masquerader: an unauthorized principal who penetrates the OS’s access controls to gain a legitimate user’s permission
- misfeasor: a legitimate user who either access resources for which he is not authorized, or misuses access to resources that he is authorized to access
- clandestine user: an individual who seizes supervisory control of the OS and uses it to evade auditing
- examples of intrusions:
- attempts to copy password file regularly
- suspicious RPC requests periodically
- multiple attempts to connect to nonexistent “bait” machines
Intrustion detection methods
- audit records
- typical audit record
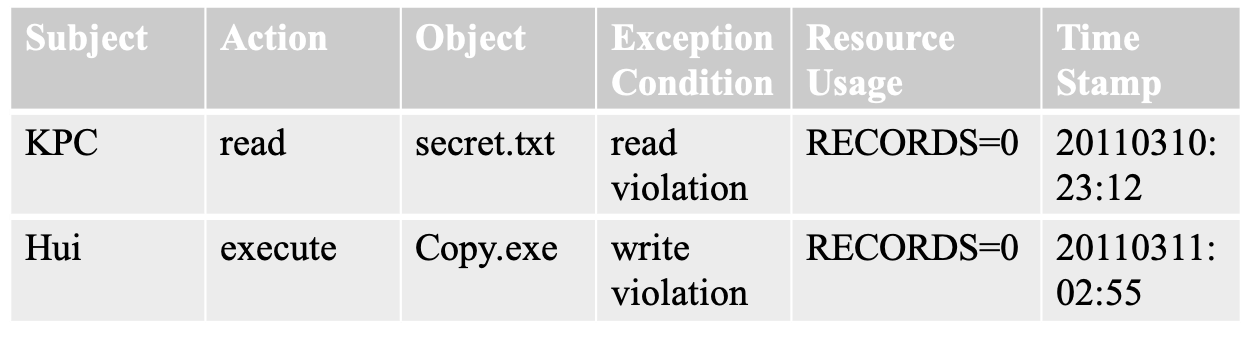
- typical audit record
- statistical intrusion detection
- 3 methods
- anomaly detection
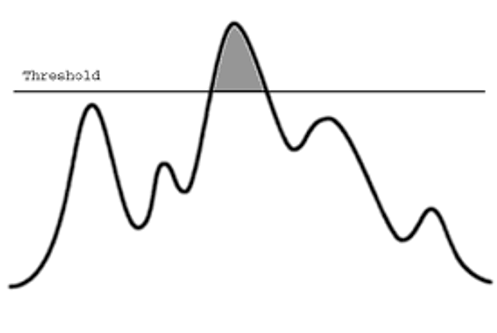
- threshold detection
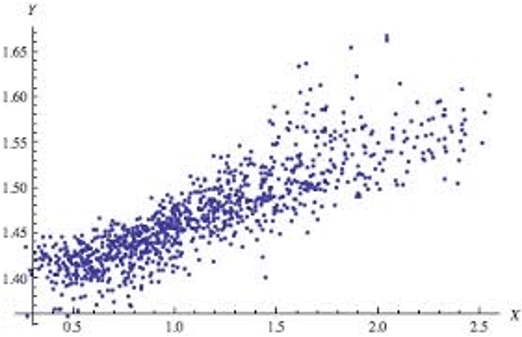
- coorelation methods (using more than one variables to find relationship)
- anomaly detection
- variables
- counter
- a count of certain event types over a period of time
- e.g. number of password failure
- gauge
- measure the current value of some entities
- e.g. number of logical connections assigned to a user application, number of messages generated by a process
- interval timer
- length of time between 2 events
- e.g. time between successive logins to an account
- resource utilization
- quantity of resources consumed in a specified period
- e.g. number of pages printed by a user session
- counter
- measurements
- mean and standard deviation
- average and variability
- intruders belongs to 0.15% in 3 sd condition (both sides are 0.3%)
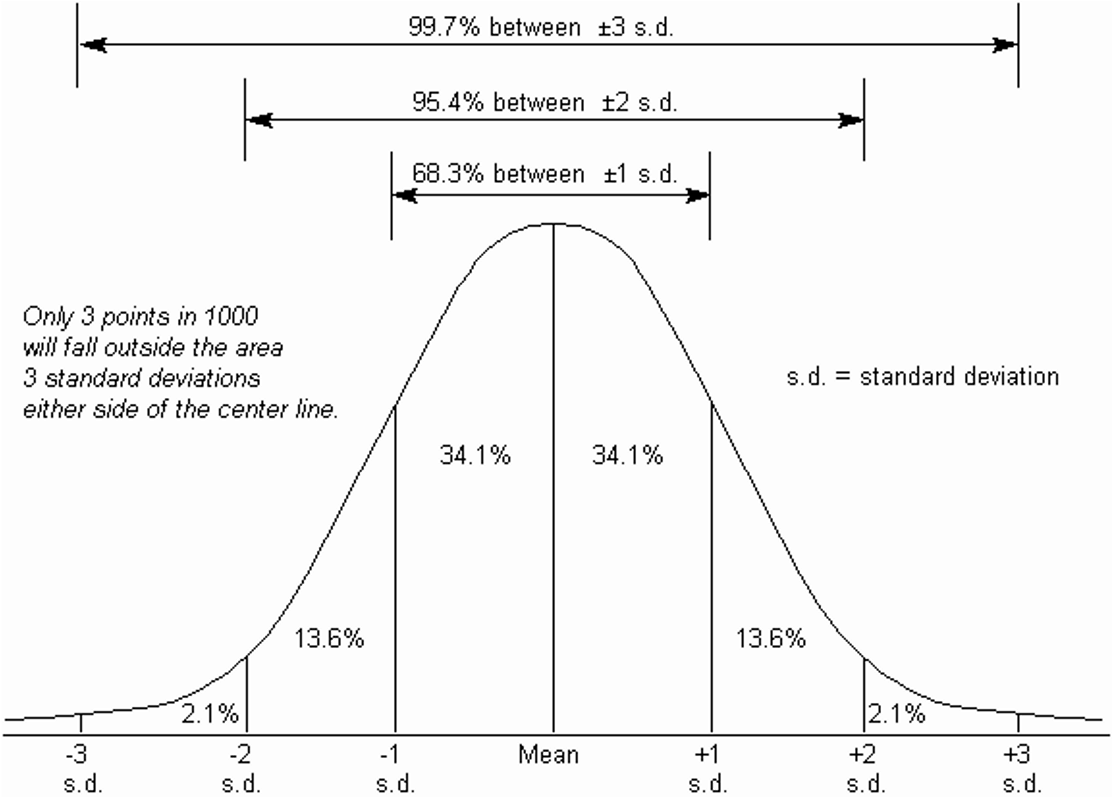
- new observation \(x_{n+1}\) is defined to be abnormal if it falls outside a confidence interval that is d standard deviations from the mean for some parameter d: \(mean + d \times stdev\)
- by Chebyshev's inequality, the probability of a value falling outside this interval is at most \(\frac{1}{d^2}\)
- example
- assume mean = 10, stdev = 3, d = 7, observe = 32
- \(mean + d \times stdev = 31\)
- \(p(observe = 32) < \frac{1}{7^2} = 0.02\)
- only 2% -> normal user, 98% -> intruder
- example
- multivariate analysis
- measure the correlation
- two variables, e.g. using time and access number to do intrustion detection
- \(r = \frac{\displaystyle \sum_i{(x_i-\overline{x})(y_i-\overline{y})}}{{\sqrt{\displaystyle \sum_i({x_i-\overline{x}})^2}}{\sqrt{\displaystyle \sum_i({y_i-\overline{y}})^2}}}\)

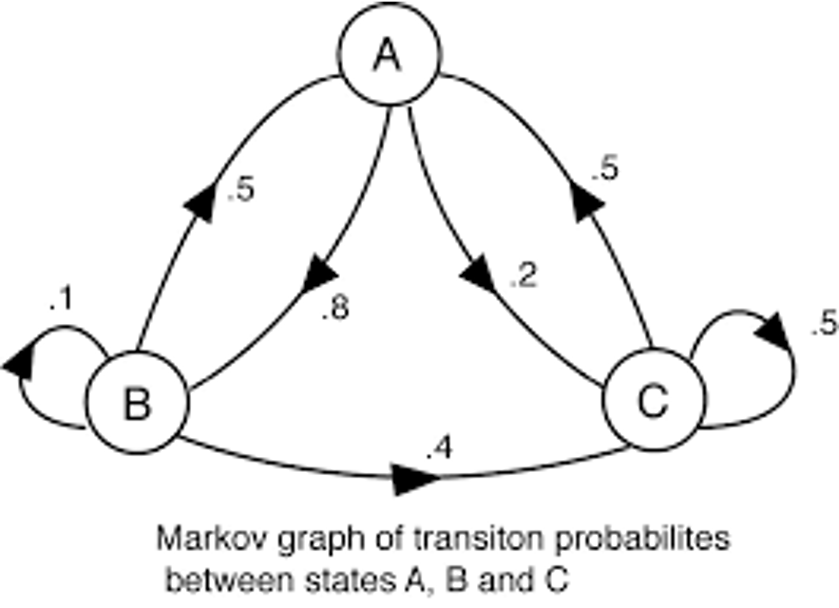
- markov process
- measure the transition among states
- e.g. transition between certain commands
- time series
- focus on time intervals, looking for sequence of events that happen too rapidly or too slowly
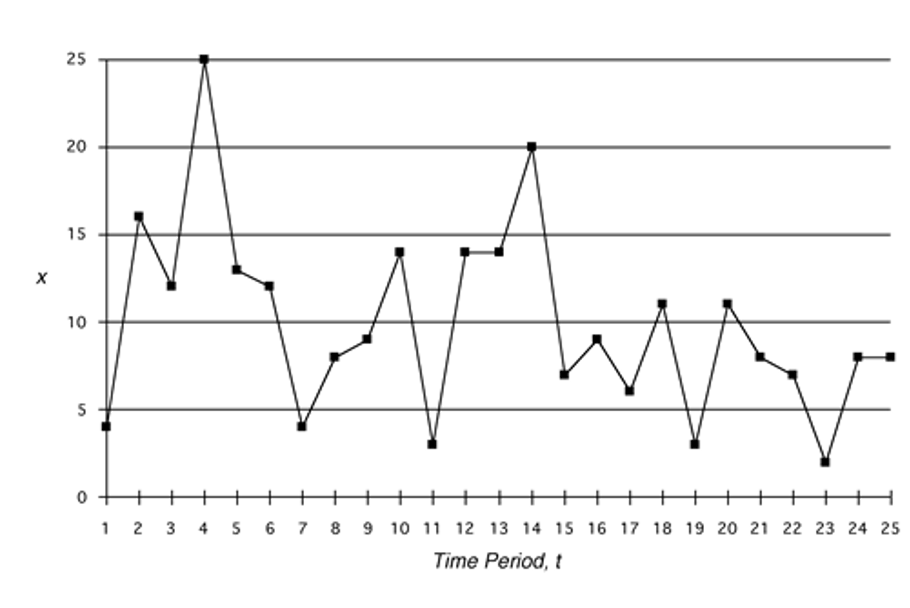
- focus on time intervals, looking for sequence of events that happen too rapidly or too slowly
- operational
- based on a judgment of what is considered abnormal, instead of based on past records
- e.g. large number of login attempts in a short period of time
- mean and standard deviation
- 3 methods
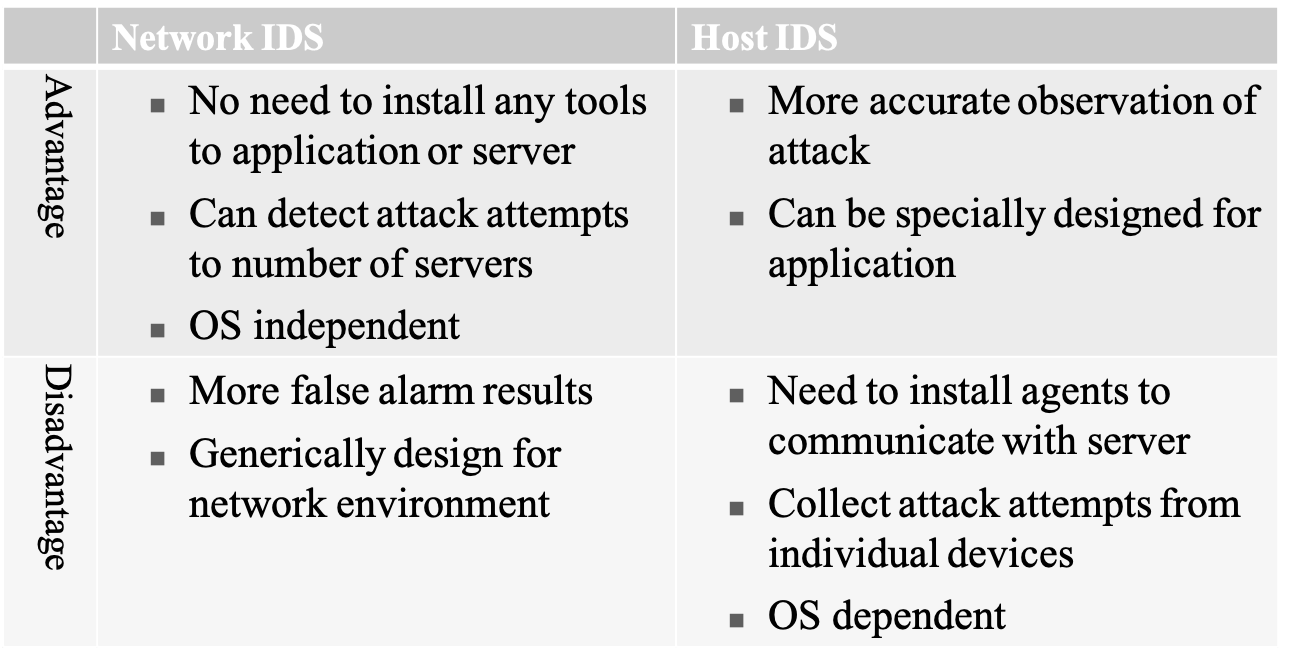
Comparison of host and network based IDS
Security Testing
Overview
- common testing only tests the application function, using some cases and scenarios
- security requirements for a system

Simple security requirement (old days)
- security requirement
- authentication: the application should use password to authenticate the user
- test cases
- login successful
- user login with a valid password
- login failure
- user fails to login with an invalid passwords
- multiple login failure
- password change
- login successful
- it is not sufficient
Real security testing (nowadays)
- security testing
- checking that some features appears to fail, e.g.
- the tester is able to spoof another user’s identity
- the tester can tamper the data
- the tester can view data he should not have access to
- the tester can deny service to other users
- checking that some features appears to fail, e.g.
- state spaces view
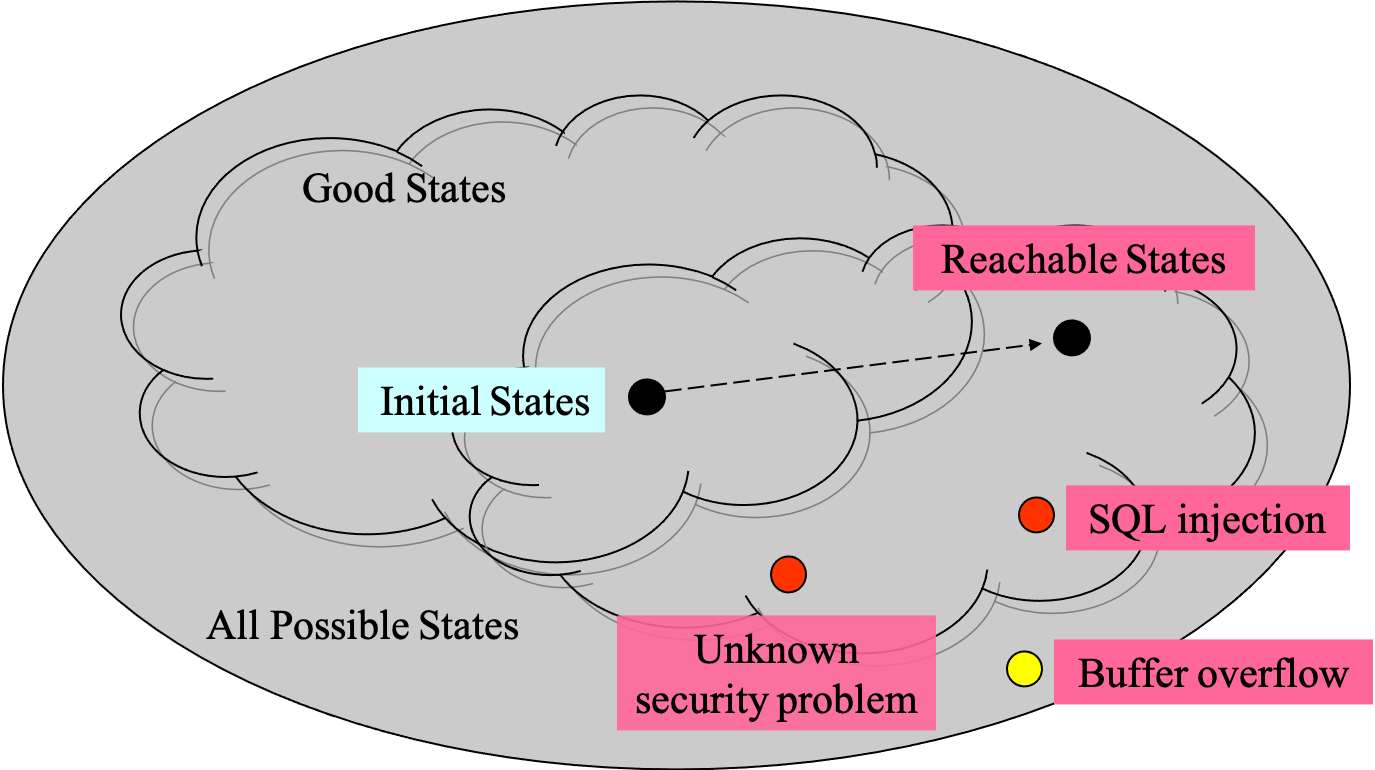
- approaches
- attack testing
- pretend to be an attacker for testing
- examples
- SQL injection
- cross-site scripting
- unexpected input
- hacking is more difficult than testing
- Howard and LeBlanc by Microsoft
- identify the component interfaces (using data flow analysis and threat model)
- rank the interfaces by potential vulnerability
- construct test cases according to well known security problems (STRIDE)
- spoofing identity
- client spoofing
- allows an attacker to pose as another user
- e.g. insecure basic HTTP authentication
- server spoofing
- allows a rogue server to pose as a valid server
- e.g. DNS spoofing
- client spoofing
- tampering with data
- malicious modification of data
- examples
- change data in a file with weak ACL (everyone)
- unauthorized update of data in the database
- repudiation
- user denies performing an action while the other party cannot prove the existence of the action
- e.g. cutomers purchase goods online
- information disclosure
- someone in the middle, just listening
- the exposure of information to individuals who are not supposed to have access to it
- examples
- read a file in a shared file system without the corresponding access right
- read data in transit between 2 computers, such as the username/password using basic HTTP authentication
- denial of service
- denies service to valid users
- e.g. a web server temporarily unavailable or unusable
- elevation of privilege
- an unprivileged user gains privileged access and thereby has sufficient access to compromise or destroy an entire system
- e.g. Trojan runs with “root” privileges and open a backdoor for the hacker
- spoofing identity
- penetration test —— a security service
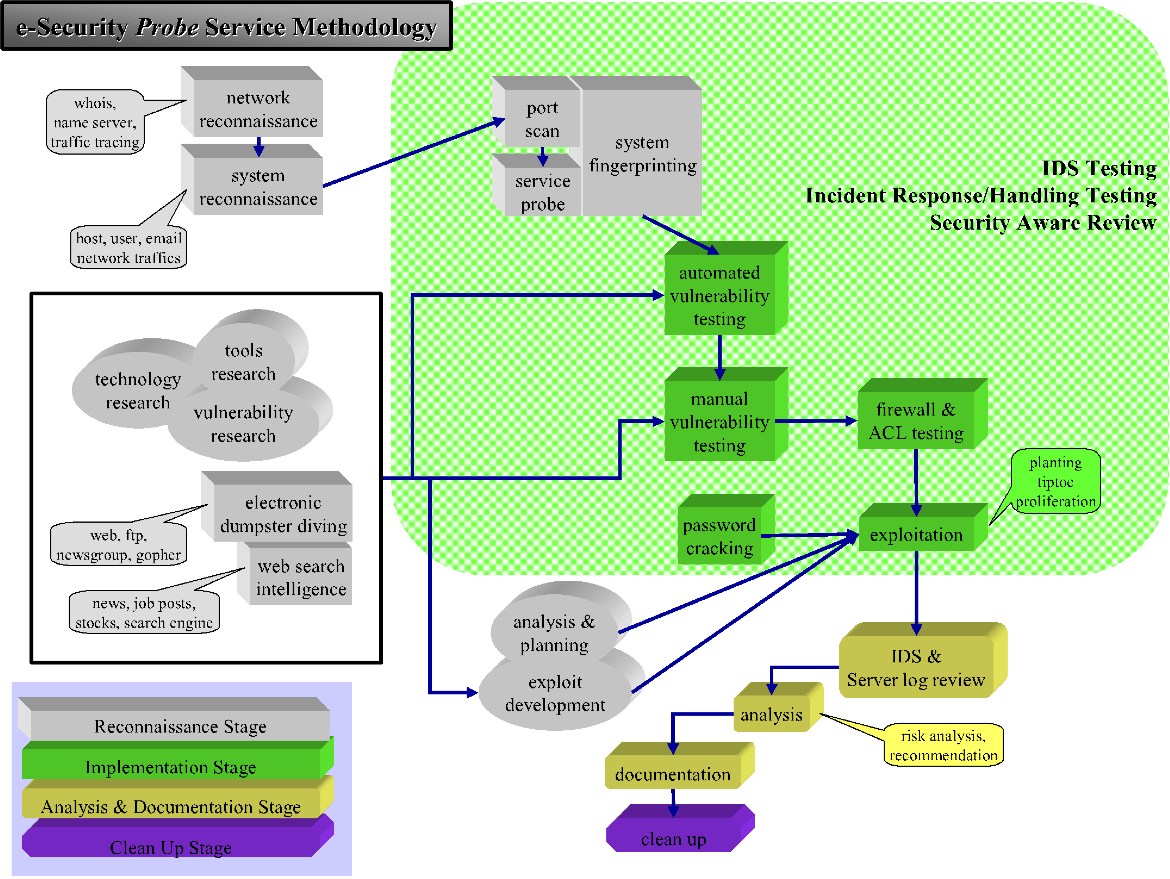
- attack testing