5 minutes
ICOM6045 Communication Network Security
Introduction
Communication network
- definition
- an infrastructure for exchanging information in electronic form
- a physical infrastructure: communication links (e.g., wires and cables)
- a logical infrastructure: protocols
- an infrastructure for exchanging information in electronic form
- types of information
- voice
- documents
- photos
- video, etc
- types of communication network
- a public switched telephone network (circuit switching, lots of switches in the telephone network, single line, more expensive)
- a mobile telephone network
- the Internet (packet switching, sharing, much cheaper)
- a communication infrastructure (i.e., a common communication network), for exchanging various types of information
Reference Model and Internet Model
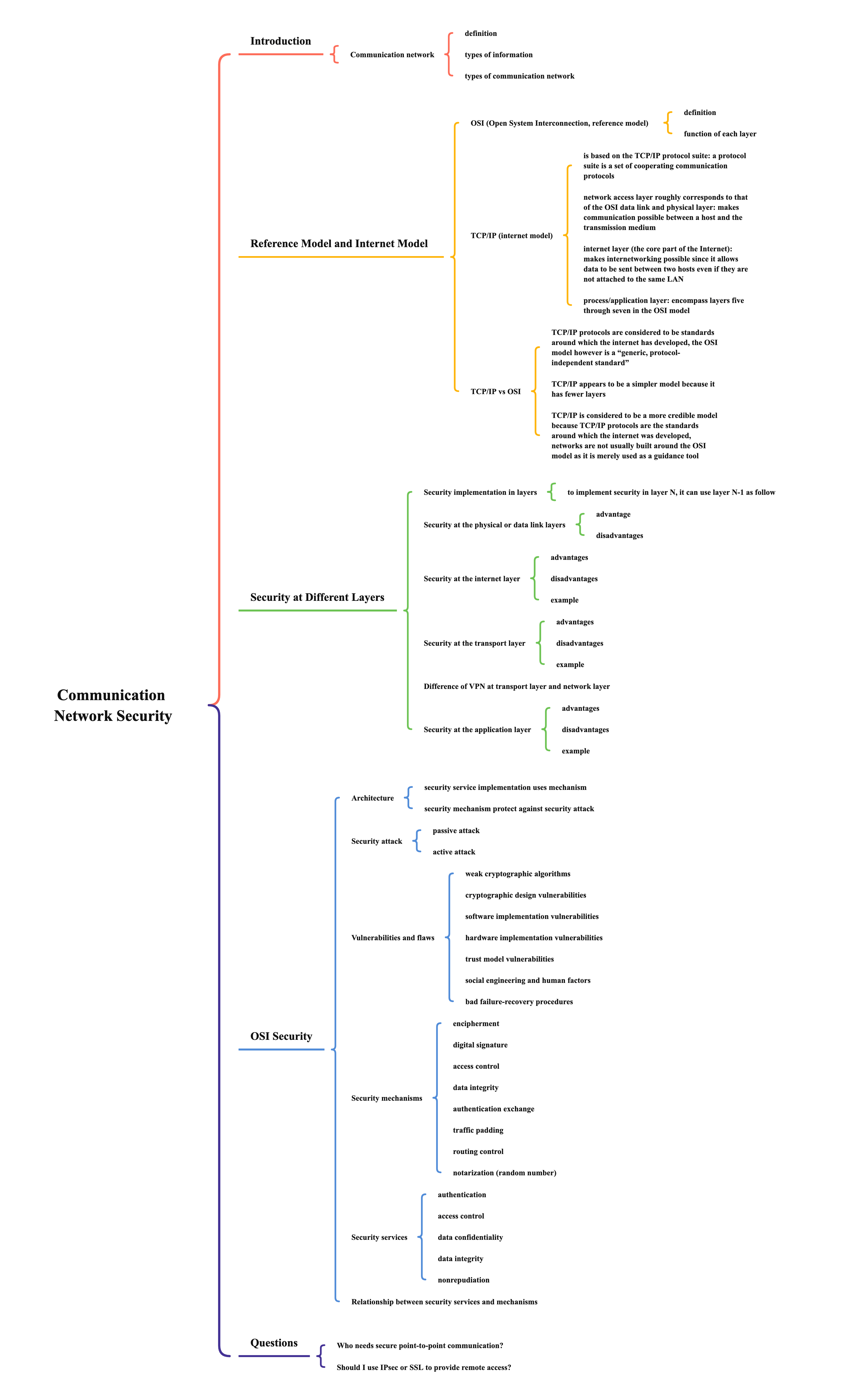
OSI (Open Systems Interconnection, reference model)
- definition
- one of the frequently used models for explaining the logical structure of a communication network
- function of each layer
- provides a subset of communication services in such a way that it uses the services from the next lower layer and provides service to the next higher layer
- H -> header, T -> trailer
- highlight
- the physical layer provides the point-to-point connection managed by the data link layer
- the data link layer establishes the “point-to-point” connection
- the network layer provides the “end-to-end” connection between two systems
- the session layer is necessary for applications that need a mechanism for establishing, managing, and terminating a session (i.e., a dialogue) between them, such as connecting to the banking system
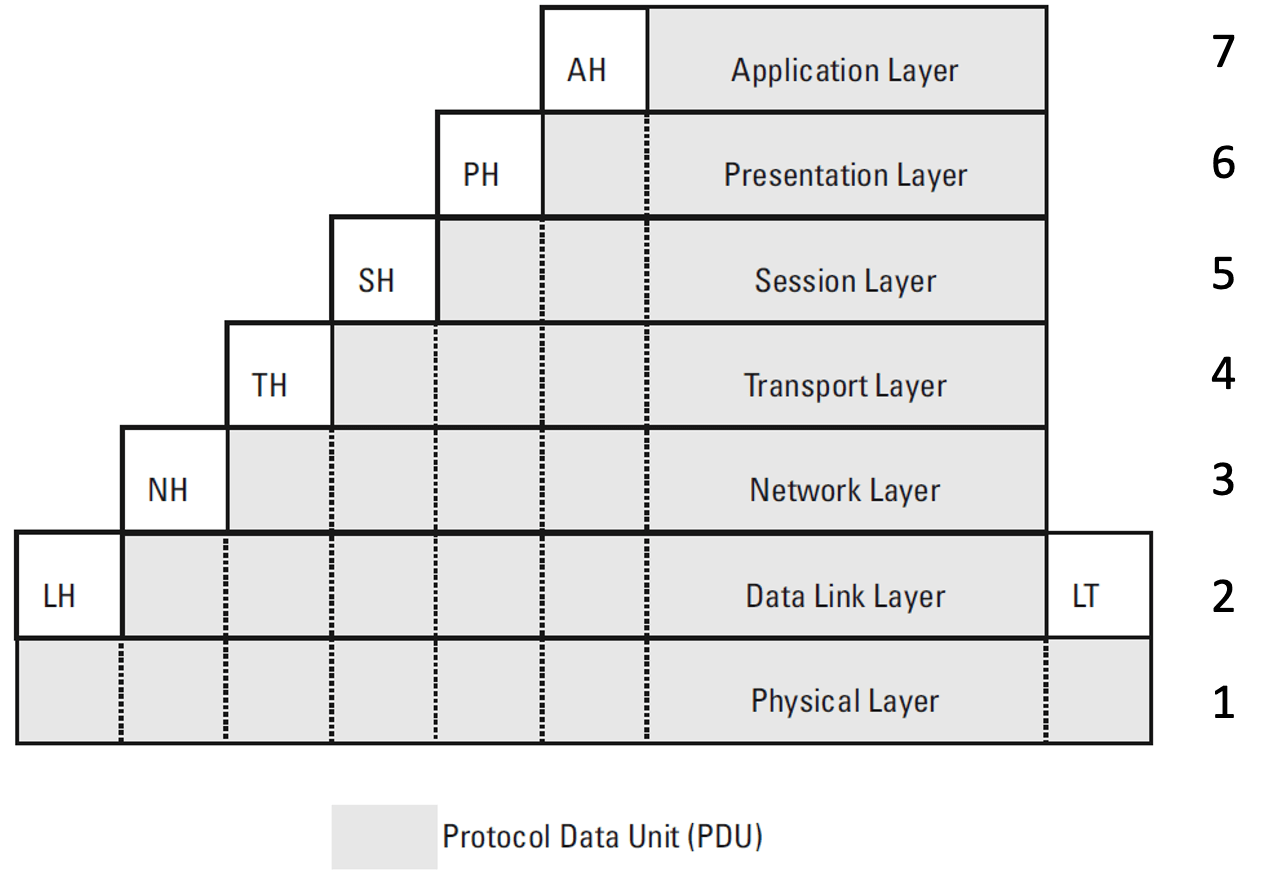
TCP/IP (internet model)
- is based on the TCP/IP protocol suite: a protocol suite is a set of cooperating communication protocols
- network access layer roughly corresponds to that of the OSI data link and physical layer: makes communication possible between a host and the transmission medium
- logical link control (LLC, IEEE 802.2 standard) sublayer
- medium access control (MAC) sublayer
- internet layer (the core part of the Internet): makes internetworking possible since it allows data to be sent between two hosts even if they are not attached to the same LAN
- transport layer (the host-host layer): supports the exchange of data between processes running on different hosts
- process/application layer: encompass layers five through seven in the OSI model
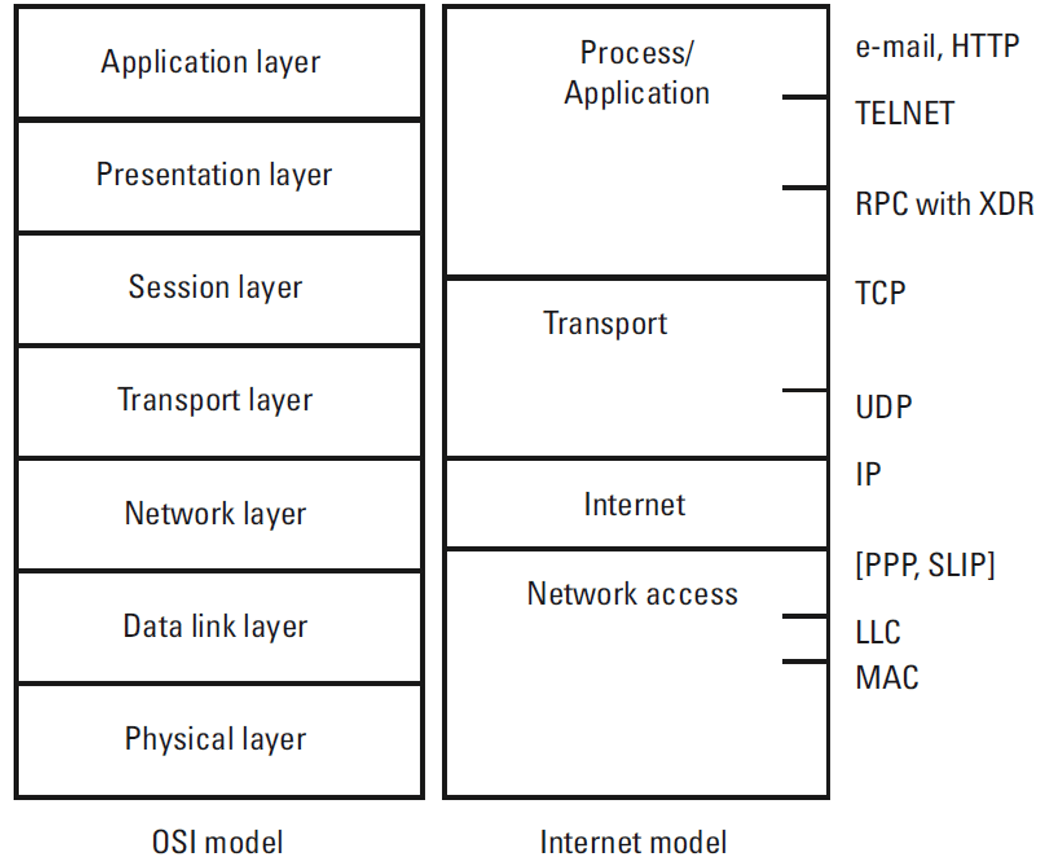
TCP/IP vs OSI
- TCP/IP protocols are considered to be standards around which the internet has developed, the OSI model however is a “generic, protocol-independent standard”
- TCP/IP appears to be a simpler model because it has fewer layers
- TCP/IP is considered to be a more credible model because TCP/IP protocols are the standards around which the internet was developed, networks are not usually built around the OSI model as it is merely used as a guidance tool
Security at Different Layers
Secruity implementation in layers
- to implement security in layer N, it can use layer N-1 as follow:
- the layer N knows the security services at the Layer N-1
- the layer N protocol has to change its calls so that they can explicitly refer to the security facilities provided
- layer N-1 security services is transparent
- the layer N protocol does not have to change
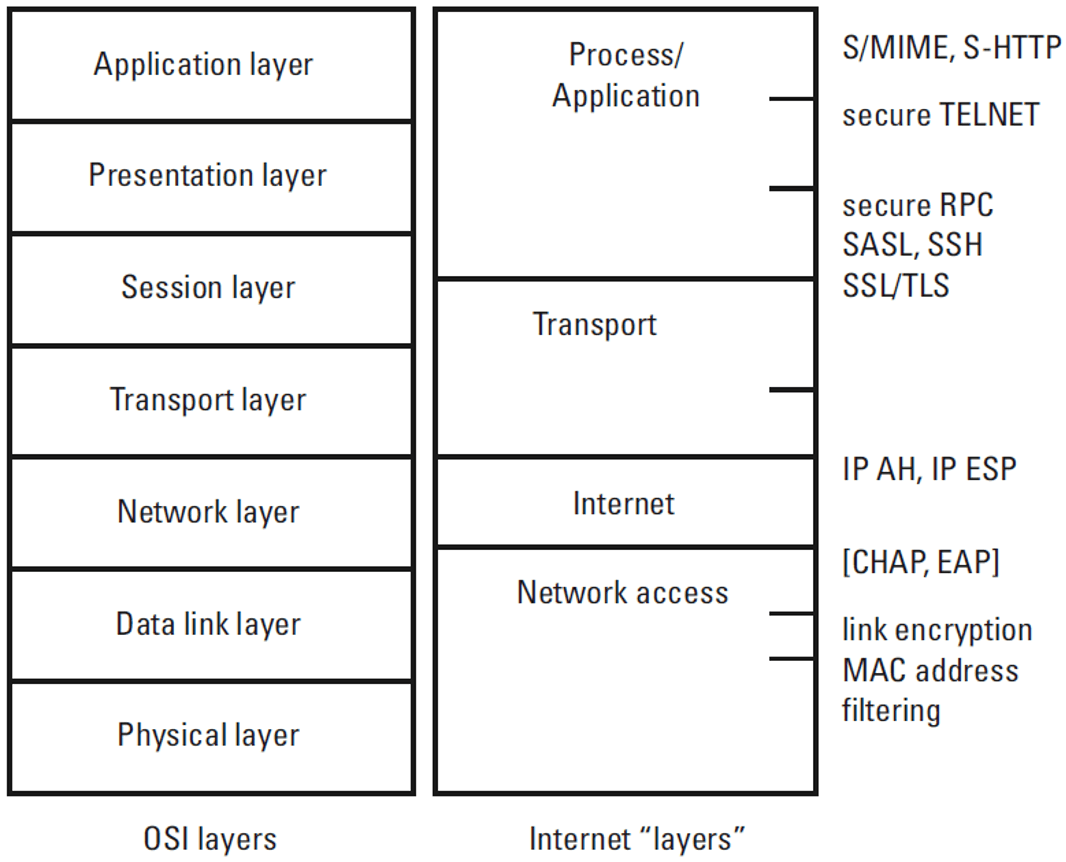
- the layer N protocol does not have to change
- the layer N knows the security services at the Layer N-1
Security at the physical or data link layers
- advantage
- provide secure point-to-point communication
- disadvantages
- cannot extend protection across heterogeneous networks
- if link-level encryption is used, each link must be equipped on both ends with an encryption device
- additionally, a message must be decrypted at each intermediate node so that the higher-level protocols can read their control information, and then encrypted again
- key management is extremely complex, because the message is decrypted at each device, it is exposed to attacks at each intermediate node, which is a severe disadvantage
Security at the internet layer
- advantages
- it is transparent to users and applications: a single tunnel secures all communications between the devices, regardless of traffic type (TCP, UDP, SNMP) or applications (email, client-server, database)
- the security software is installed and maintained by experienced system administrators, which makes it less likely to contain malicious code
- disadvantages
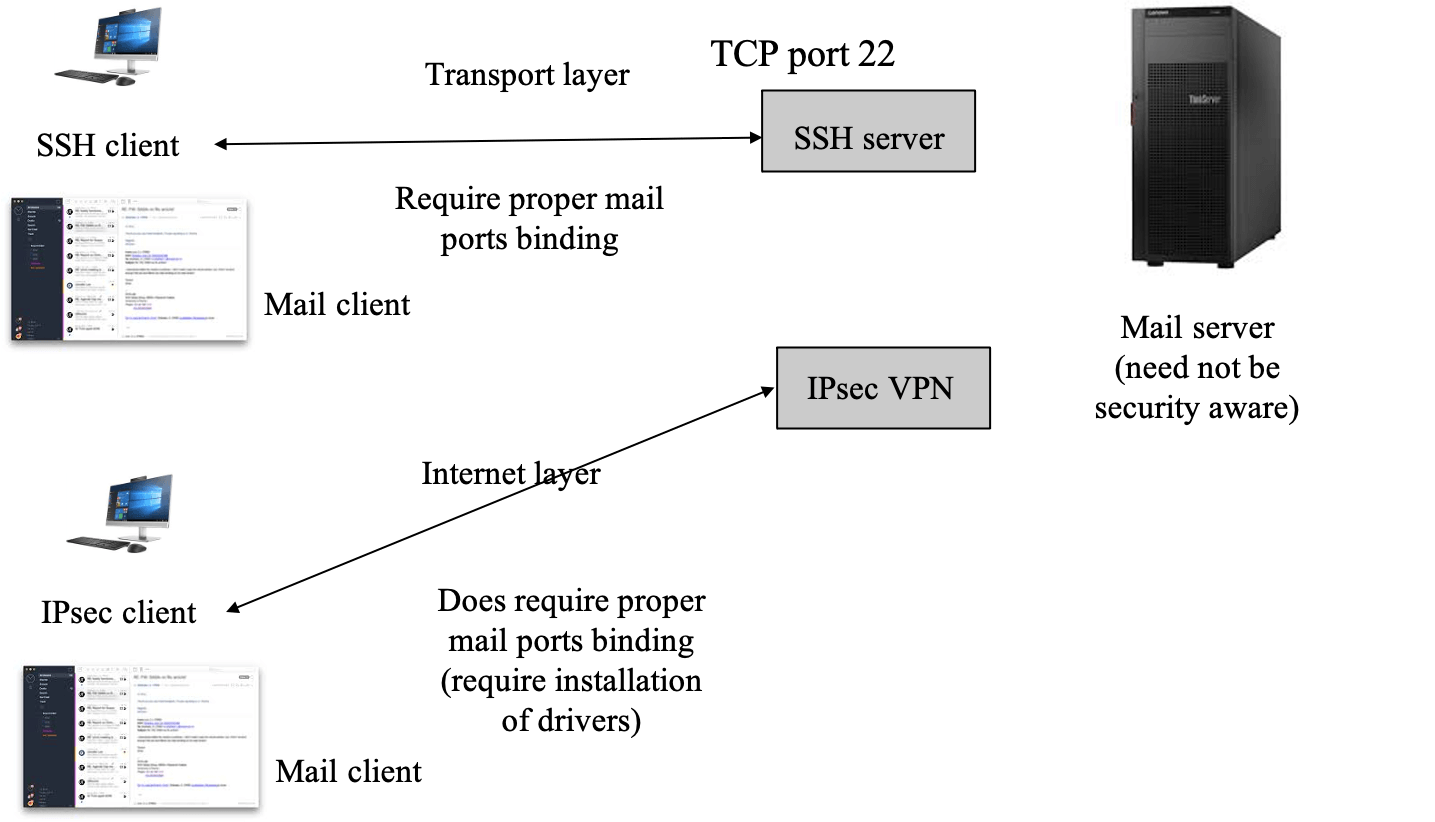
- internet-layer security requires changes to the underlying operating system, but today, we can install drivers to address it
- it is necessary that all communicating hosts use compatible versions of network security software
- example
- VPN with IPsec
Security at the transport layer
- advantages
- no change to the OS (the key difference, compared with IPsec)
- some enterprises use special purpose SSL VPN gateways that are deployed at the edge of the corporate network and serve as a proxy to internal applications, e.g. email, file servers
- disadvantages
- each application must be security aware, i.e. use corresponding function calls: each security application is secured one at a time
- the transport security library must be installed and maintained by the system administrator so that all applications running on a host can use it
- example
- VPN tunnel using SSL
Difference of VPN at transport layer and network layer
Security at the application layer
- advantages
- it involves no changes in the operating system since only a secure application must be installed
- it offers better end-to-end security since the setup and cryptographic computations take place outside the operating system
- the security functionality can be developed to fulfill the application requirements exactly
- disadvantages
- it may require more complex negotiations and setup between communicating processes
- secure applications are often installed by inexperienced users, which makes the danger of malicious code quite high
- example
- e-banking login
OSI Security
Architecture
- security service implementation uses mechanism
- security mechanism protect against security attack
Security attack
- passive attack
- eavesdropping on or monitoring of transmission to
- obtain message content
- perform traffic analysis (encrypted messages, but can analyze communication density)
- eavesdropping on or monitoring of transmission to
- active attack
- modification of data stream or creation of false data stream to
- masquerade
- replay
- modify messages
- modify control information
- infiltration
- perform denial of service
- modification of data stream or creation of false data stream to
Vulnerabilities and flaws
- weak cryptographic algorithms
- cryptographic design vulnerabilities
- software implementation vulnerabilities
- hardware implementation vulnerabilities
- trust model vulnerabilities
- social engineering and human factors
- bad failure-recovery procedures
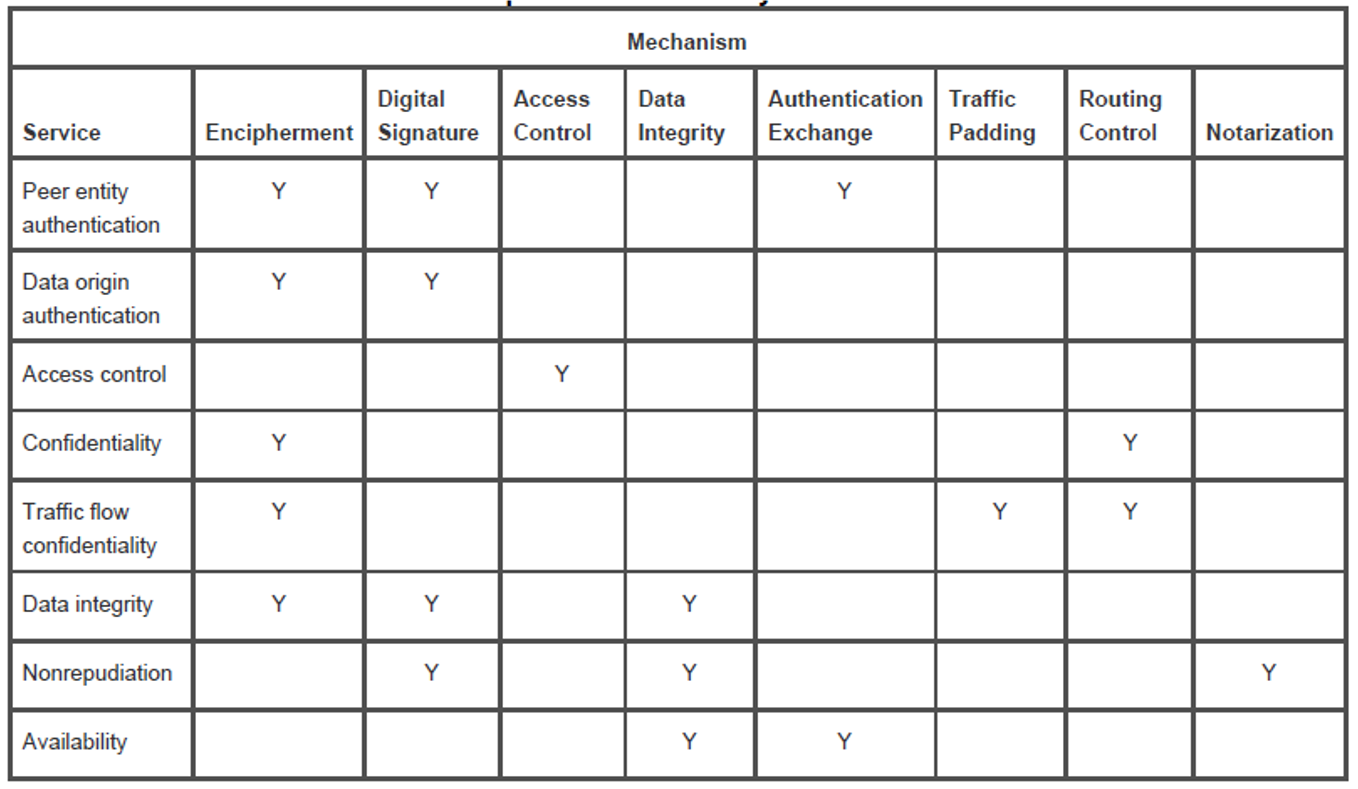
Security mechanisms
- encipherment
- digital signature
- access control
- data integrity
- authentication exchange
- traffic padding
- routing control
- notarization (random number)
Security services
- authentication
- access control
- data confidentiality
- data integrity
- nonrepudiation
Relationship between security services and mechanisms
Questions
Q: Who needs secure point-to-point communication?
A: Military and government may use the point-to-point link, which is very secure but expensive and complex. In industry, we do not use this because of cost.
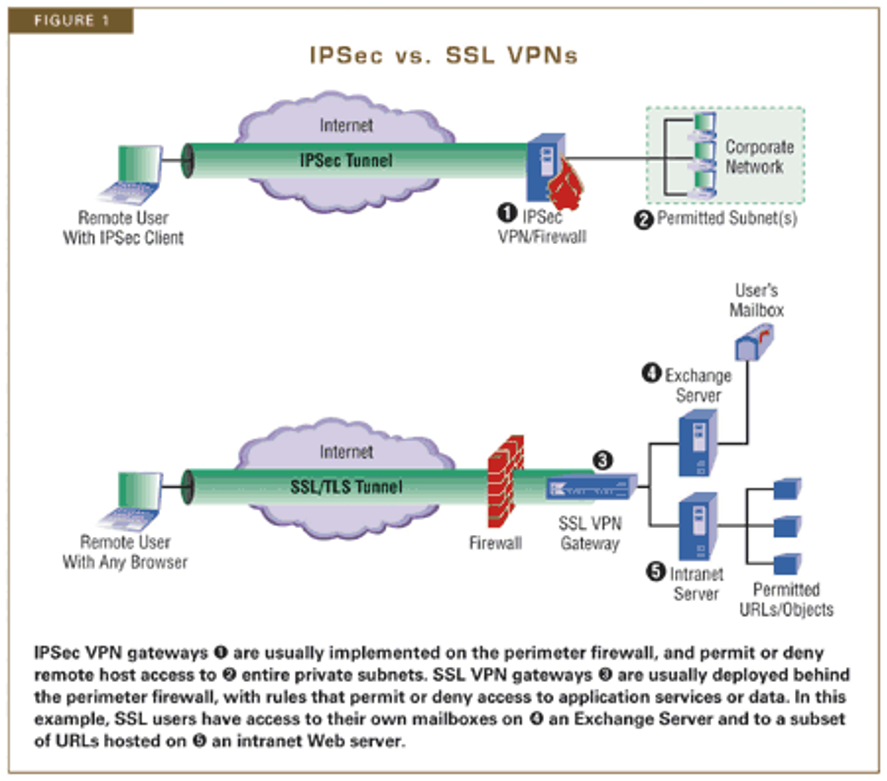
Q: Should I use IPsec or SSL to provide remote access?
A: 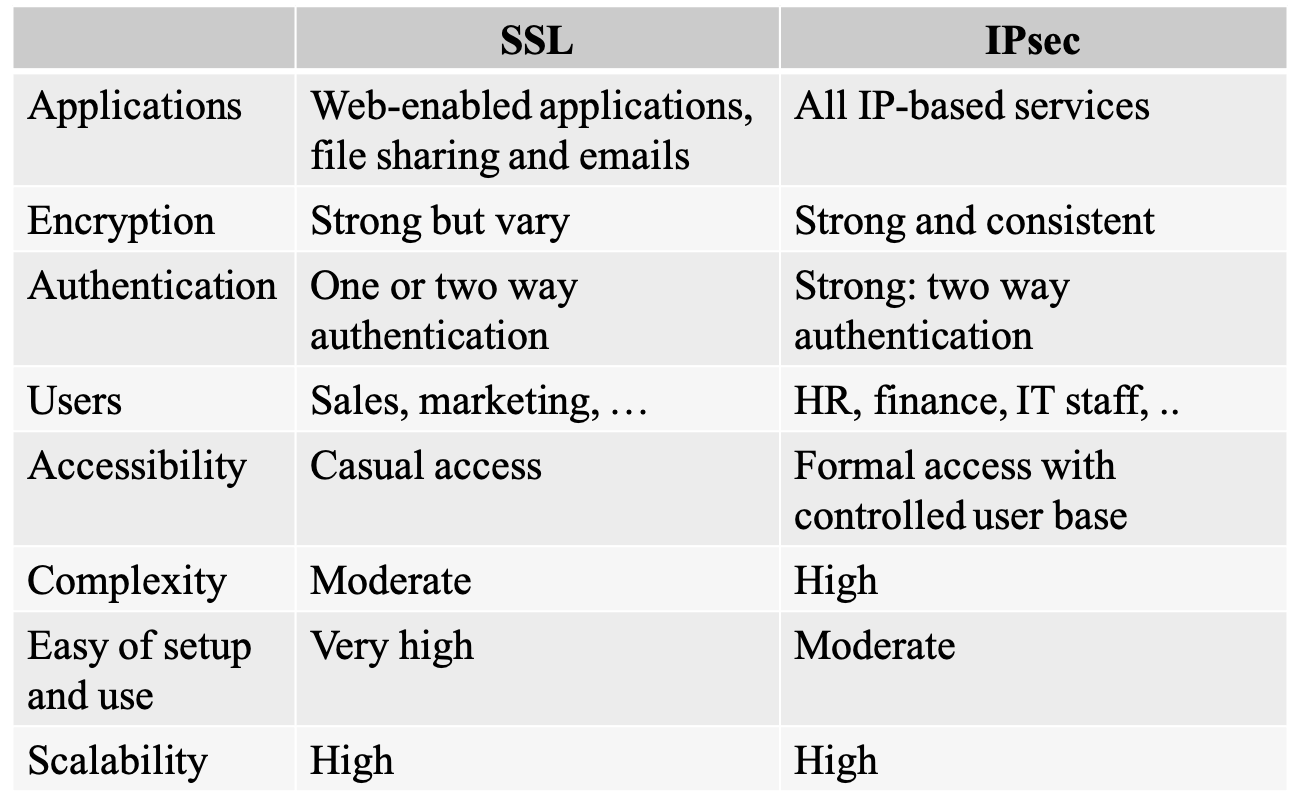
icom6045 fundamentals of e-commerce security communication network security
1003 Words
2020-12-01 11:19